Scripts
Basics- My Doubts and Confusions
So, I was watching a video by The Hated One, and they recommended setting the security level to “Safest” in Tor Browser’s settings. This disables features like JavaScript for better security. To unbreak websites, the video suggested using the NoScript add-on.
I realized that NoScript and Tor Browser’s security settings are not different; they are synced. For example, changes in Tor settings directly affect NoScript.
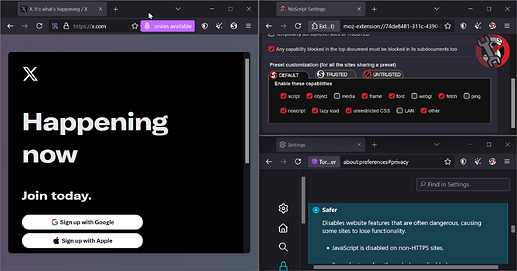
See how NoScript updates dynamically when I change settings in Tor Browser:
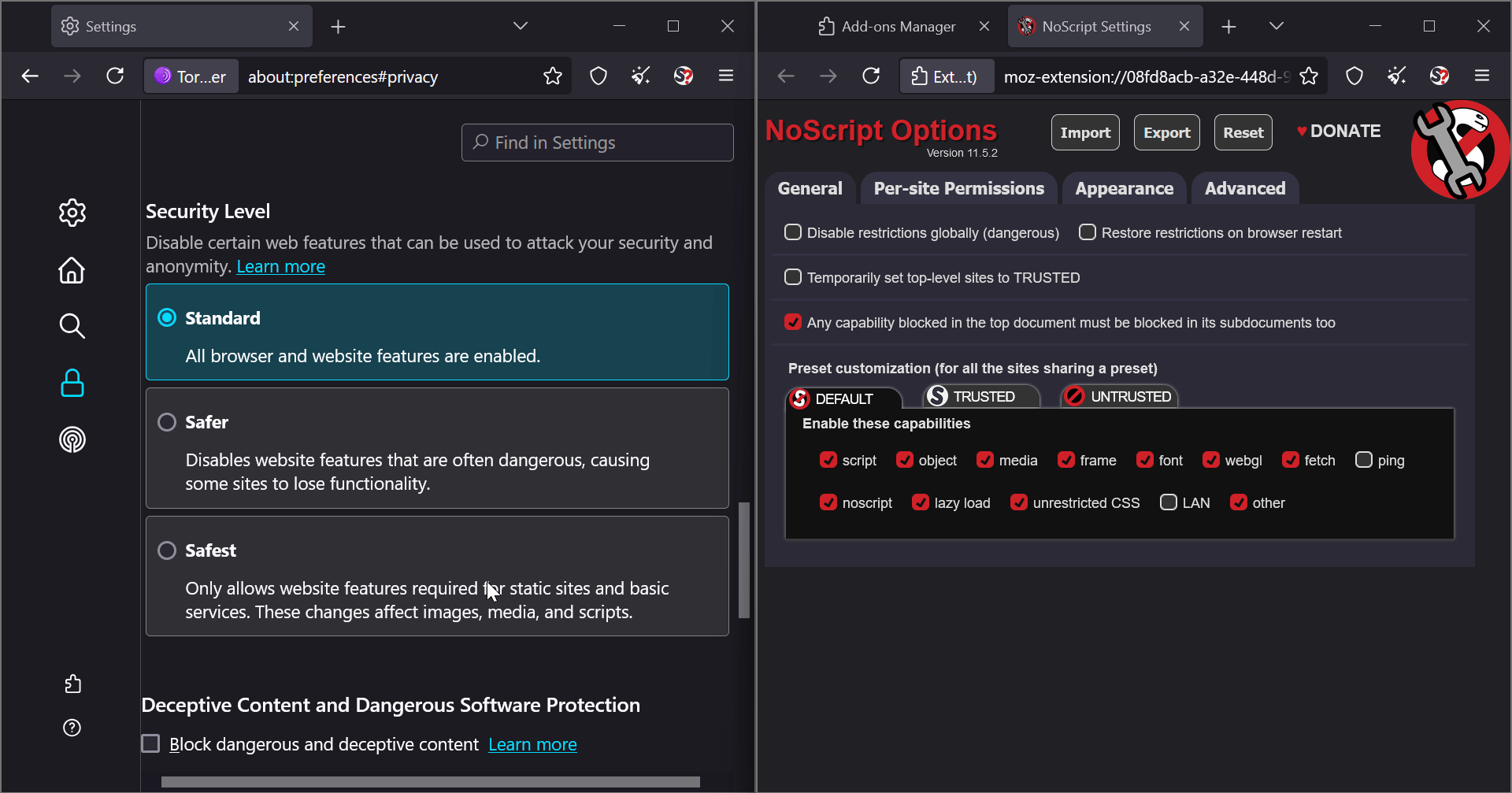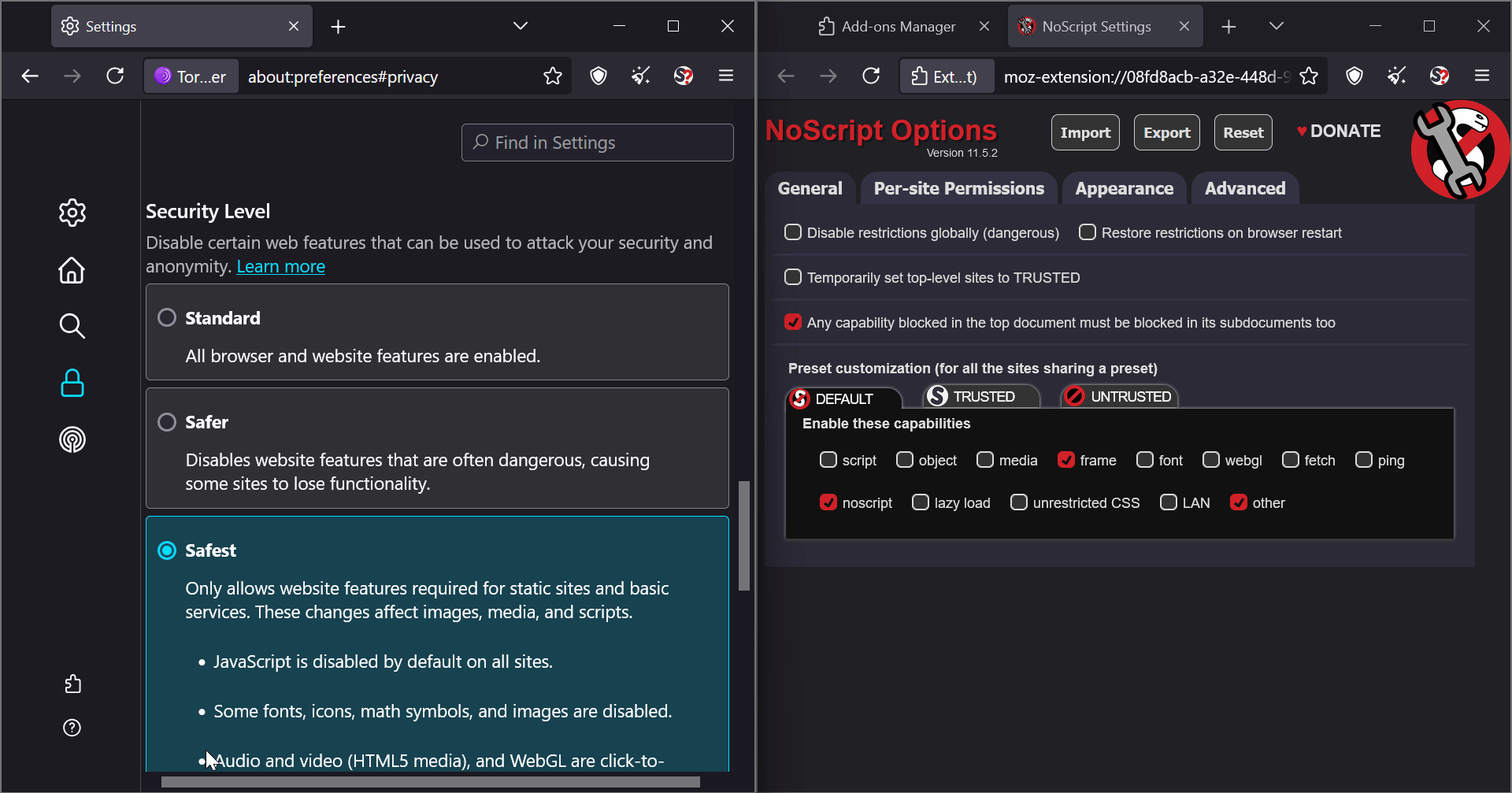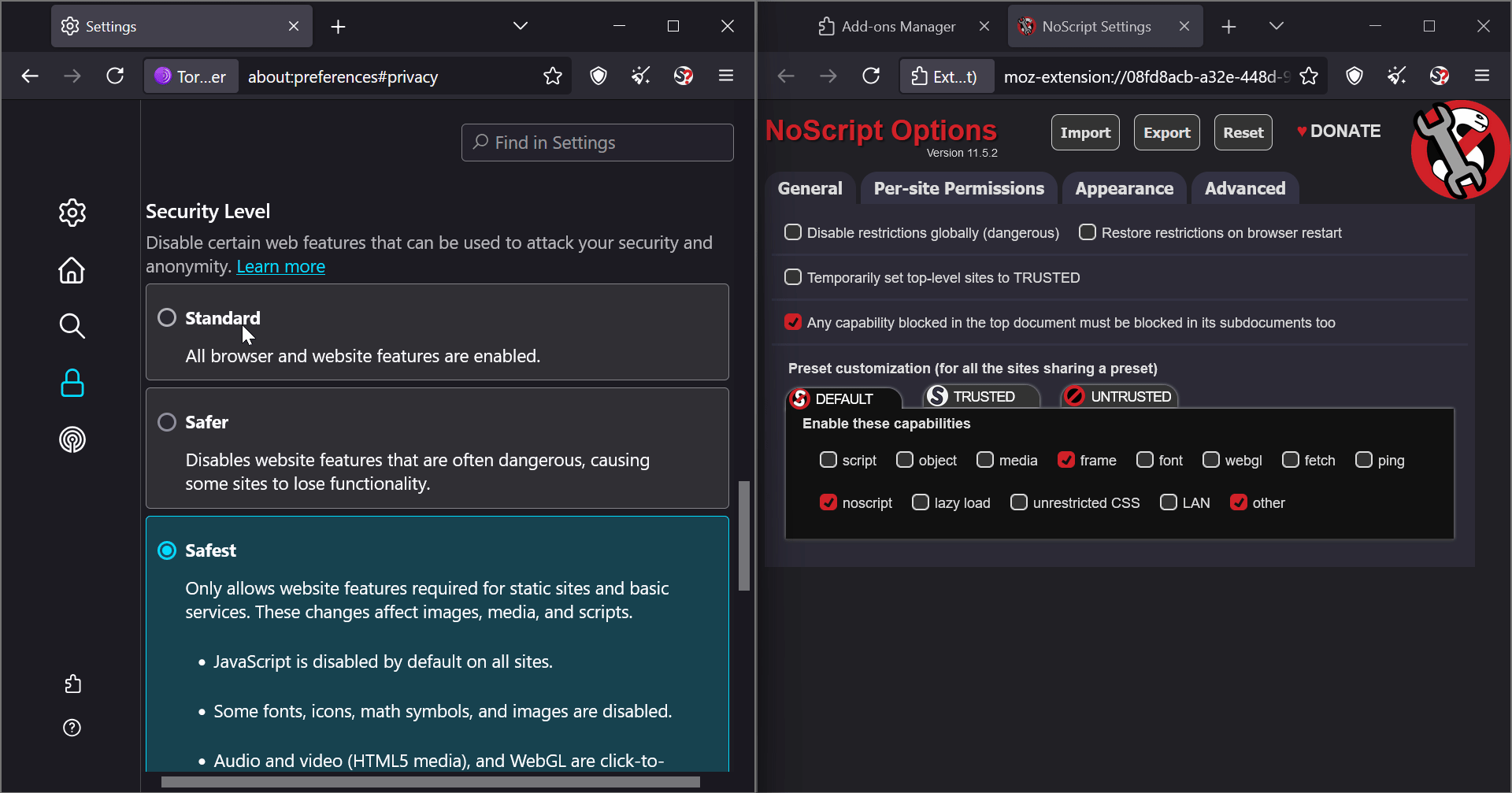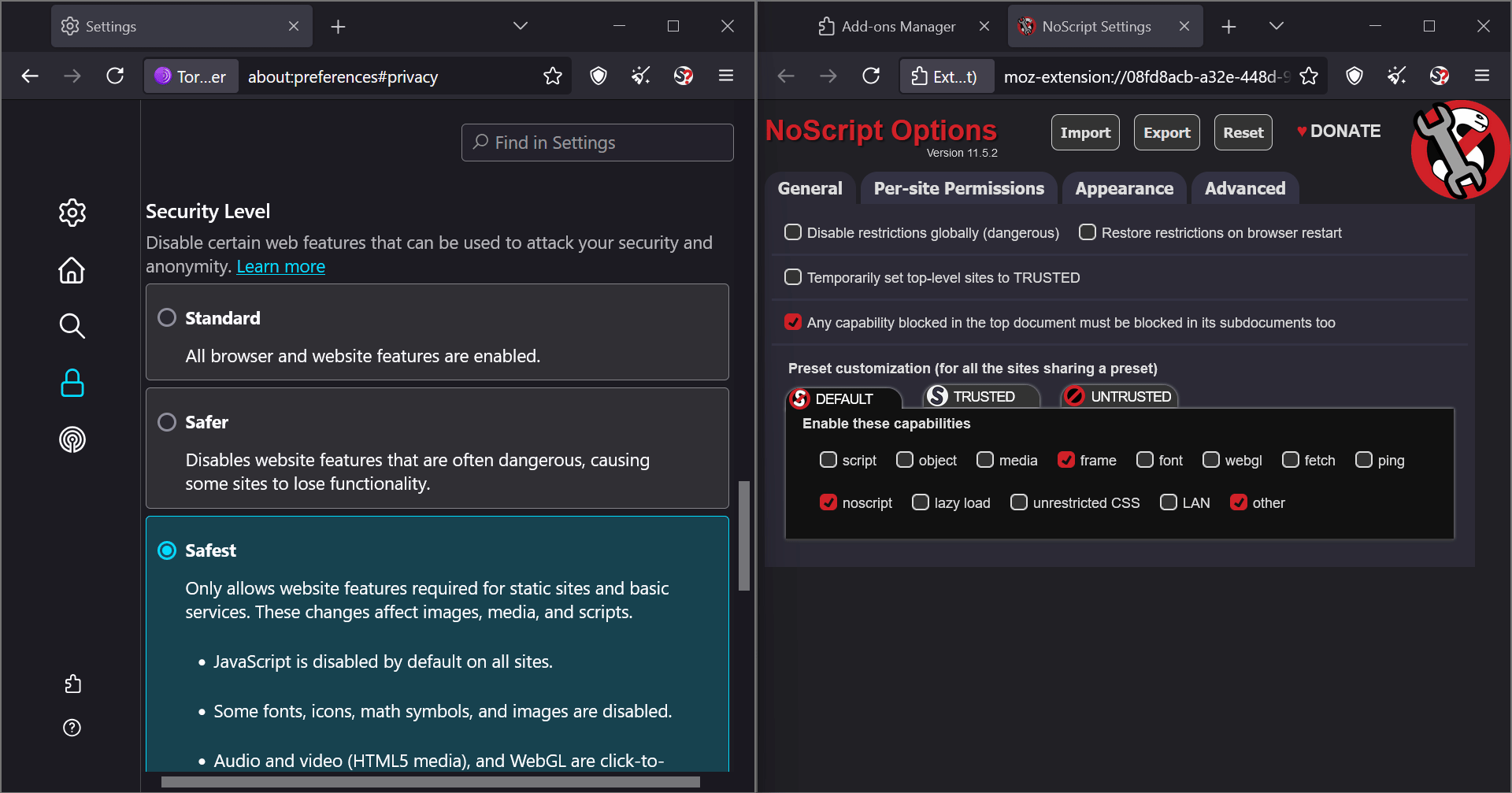
BTW By default, NoScript is not visible in the toolbar. I had to enable it from the add-ons manager.
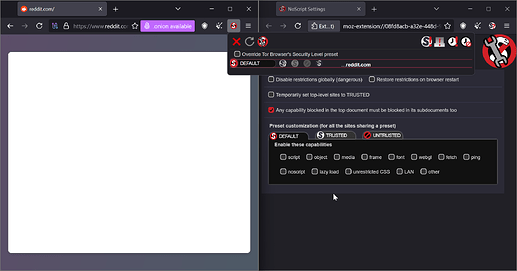
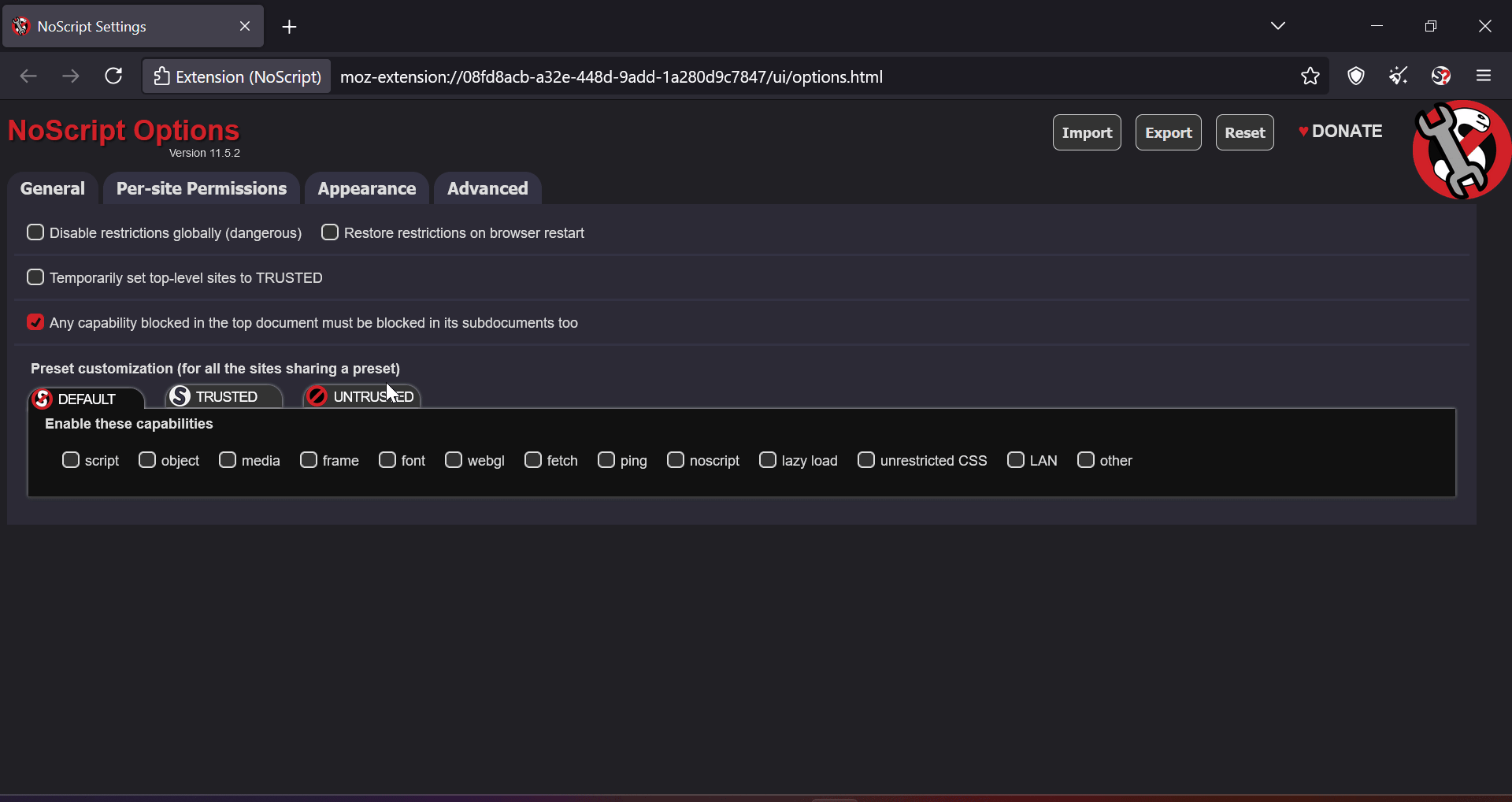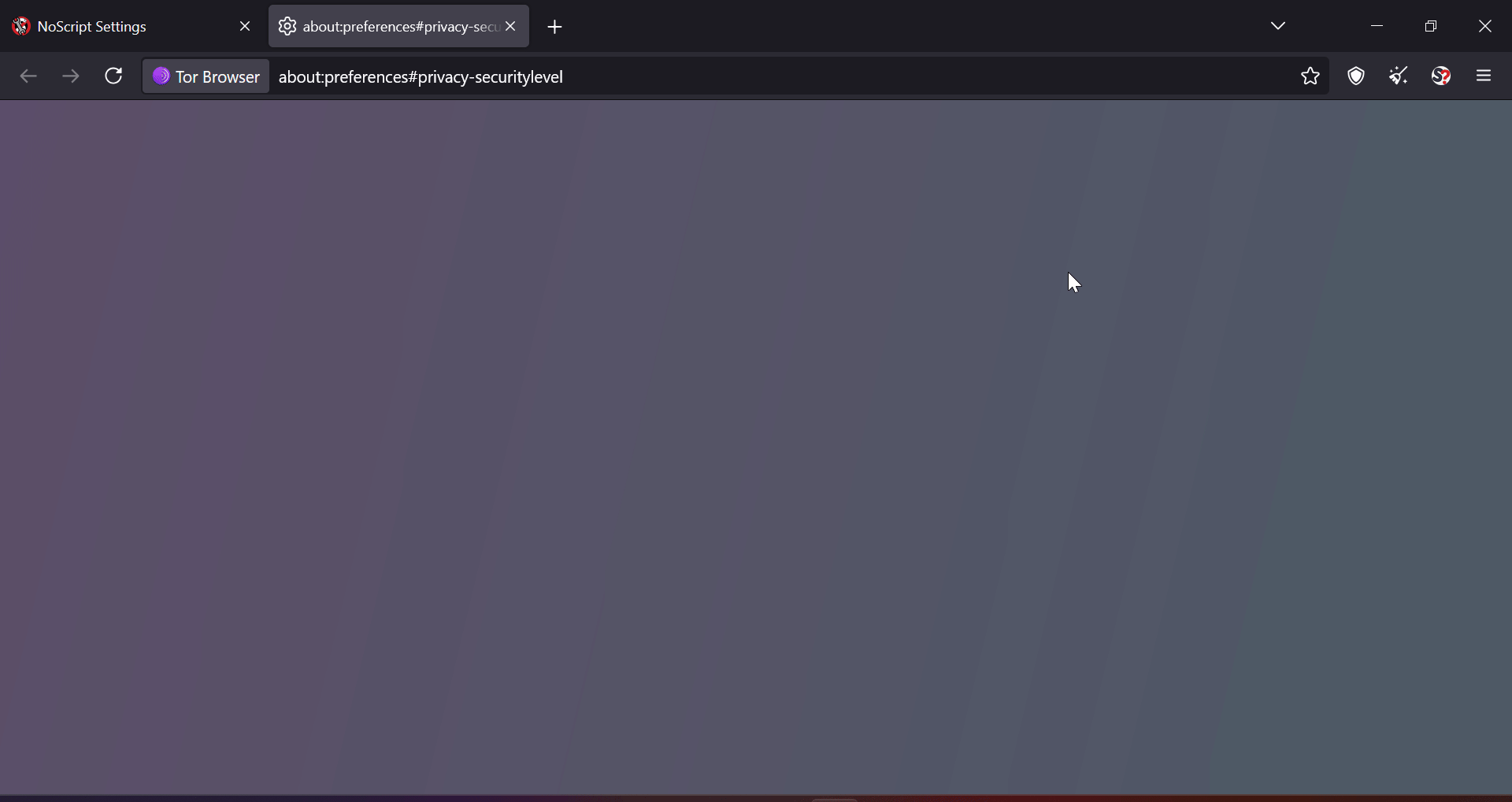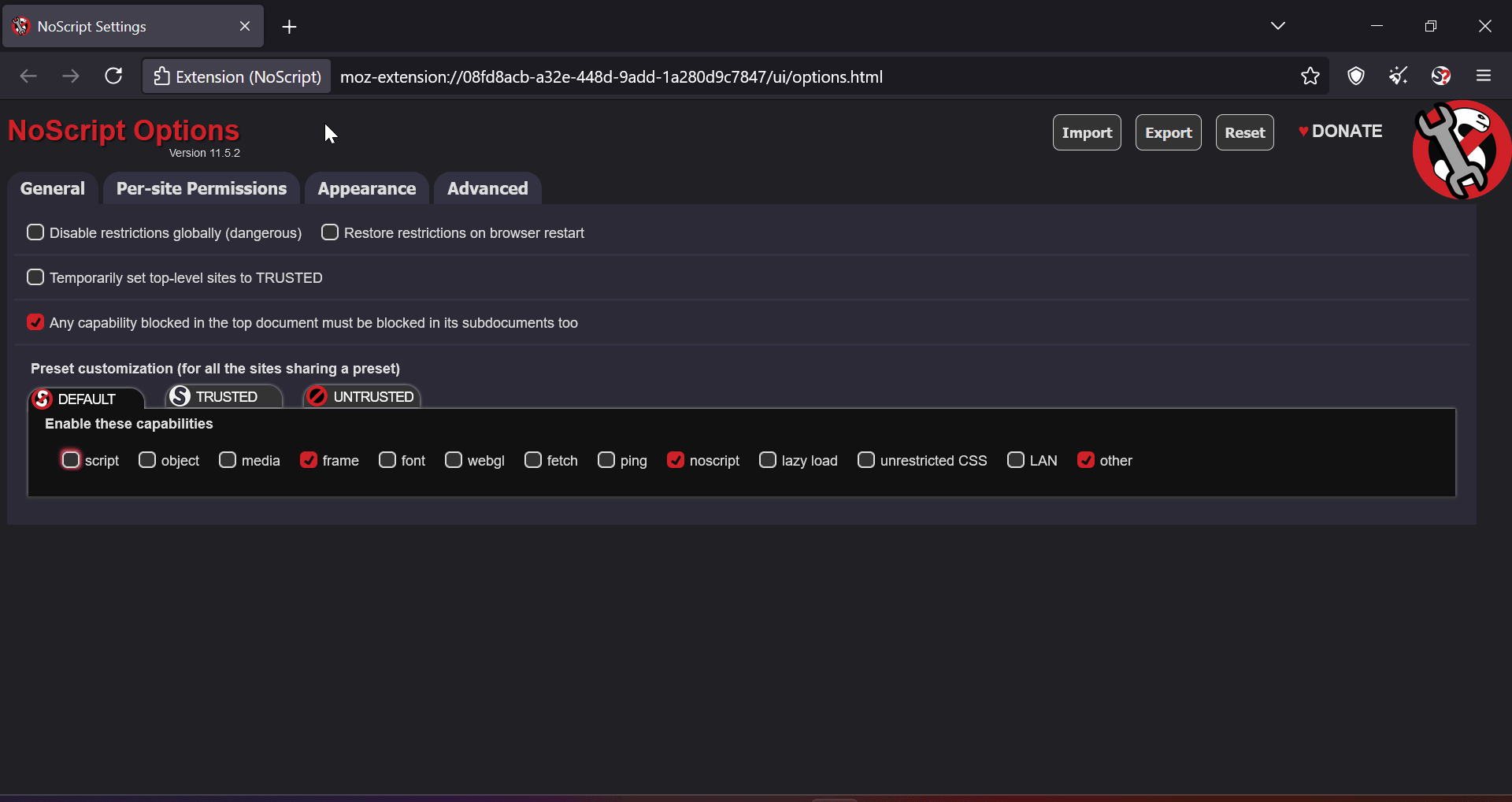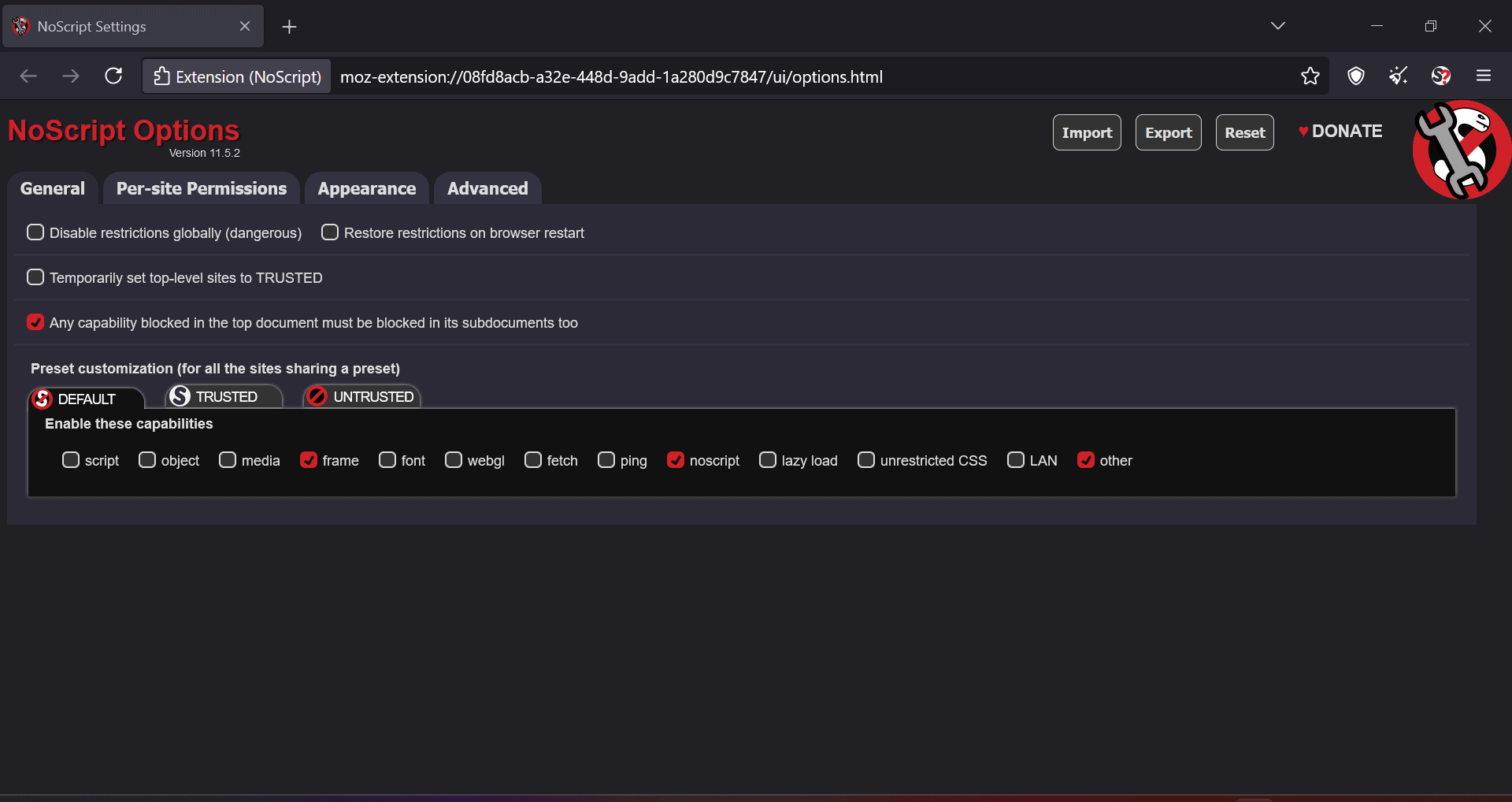
I set the security level to “Safest” and tried to unbreak websites like Reddit. Here’s what I found:
If I disable everything in NoScript settings (see below), why does it still load some content? Let’s take DuckDuckGo for eg:
Is it because certain elements in DuckDuckGo are just plain HTML? But shouldn’t “Other” settings cover that?
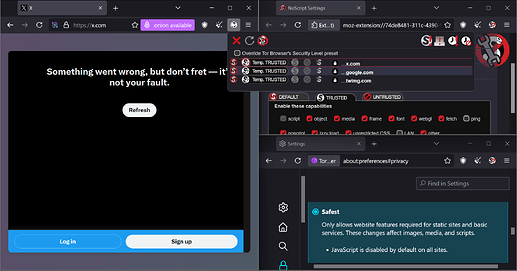
Reddit, however, doesn’t load in the same way:
btw Resetting NoScript to default settings/preset is easy; I just toggle the security level in Tor Browser back and forth:
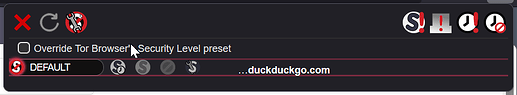
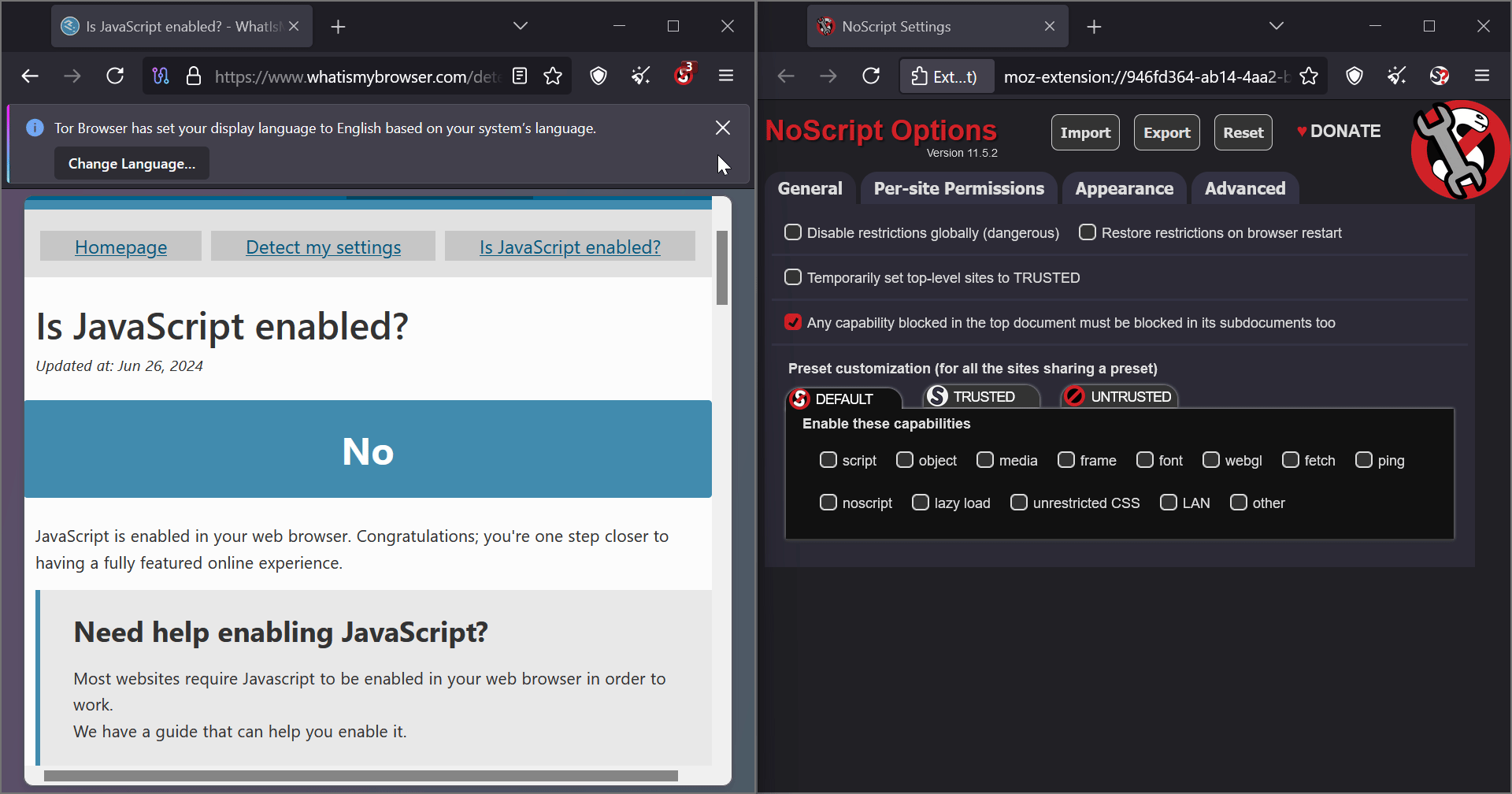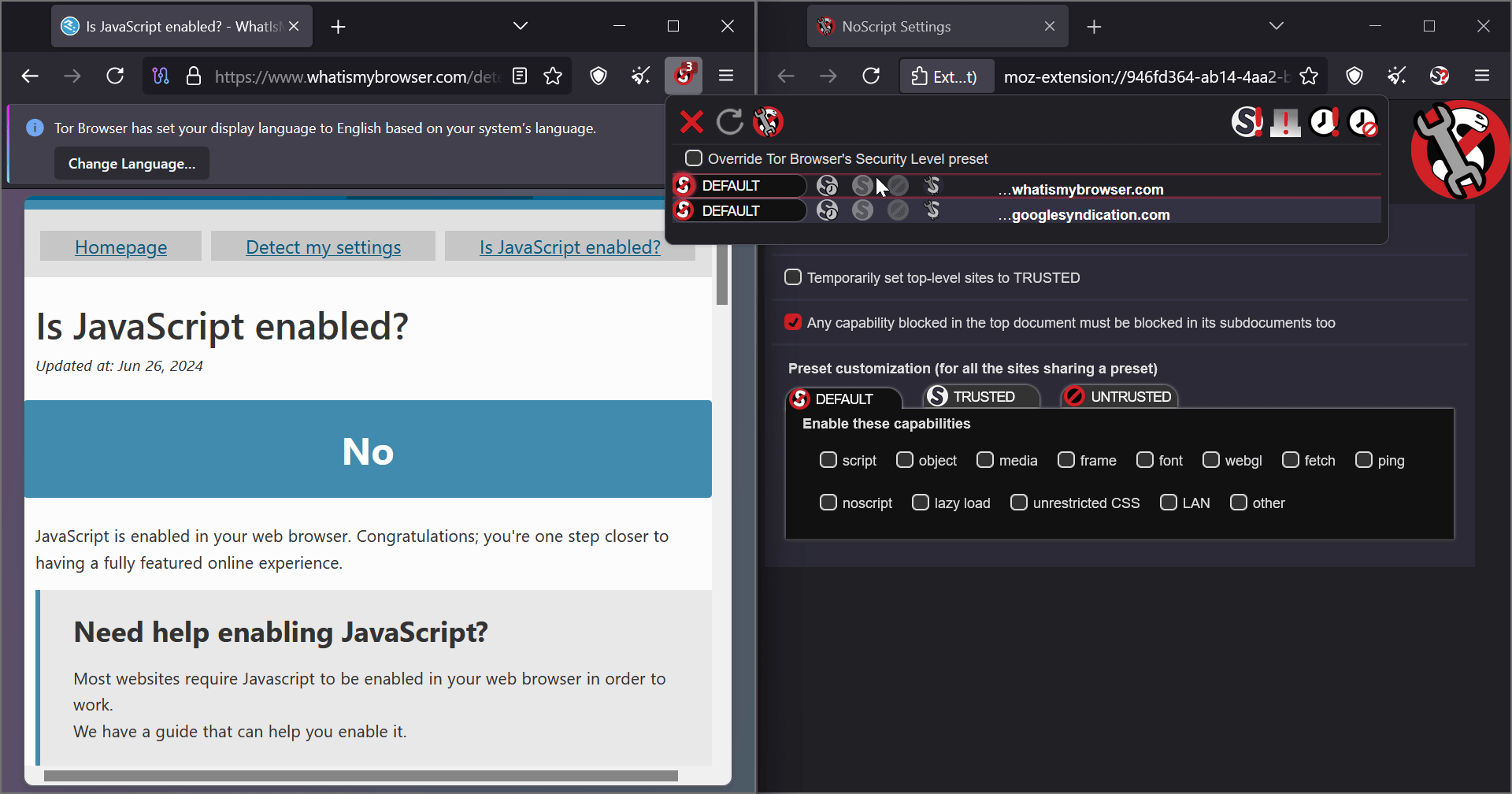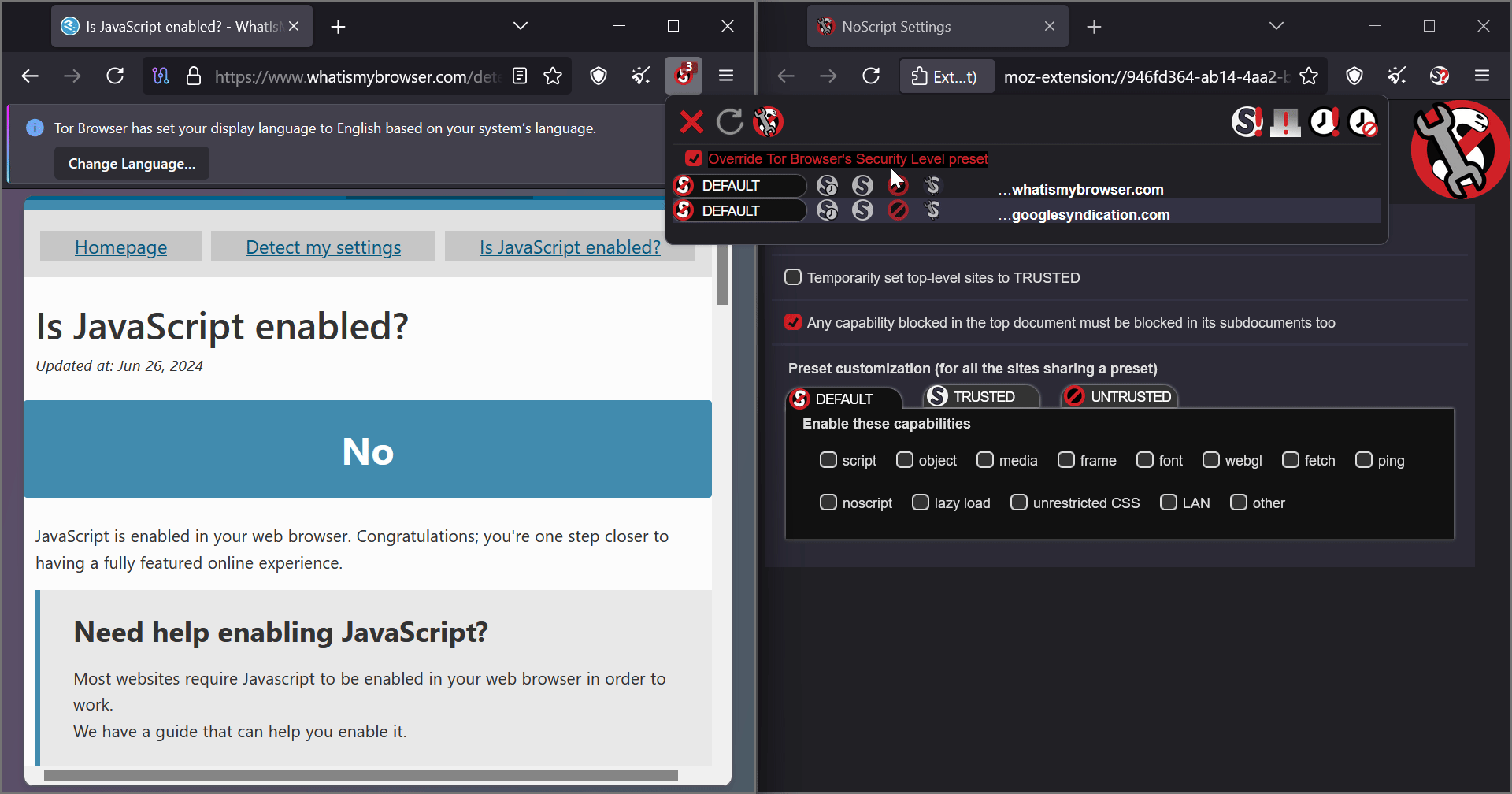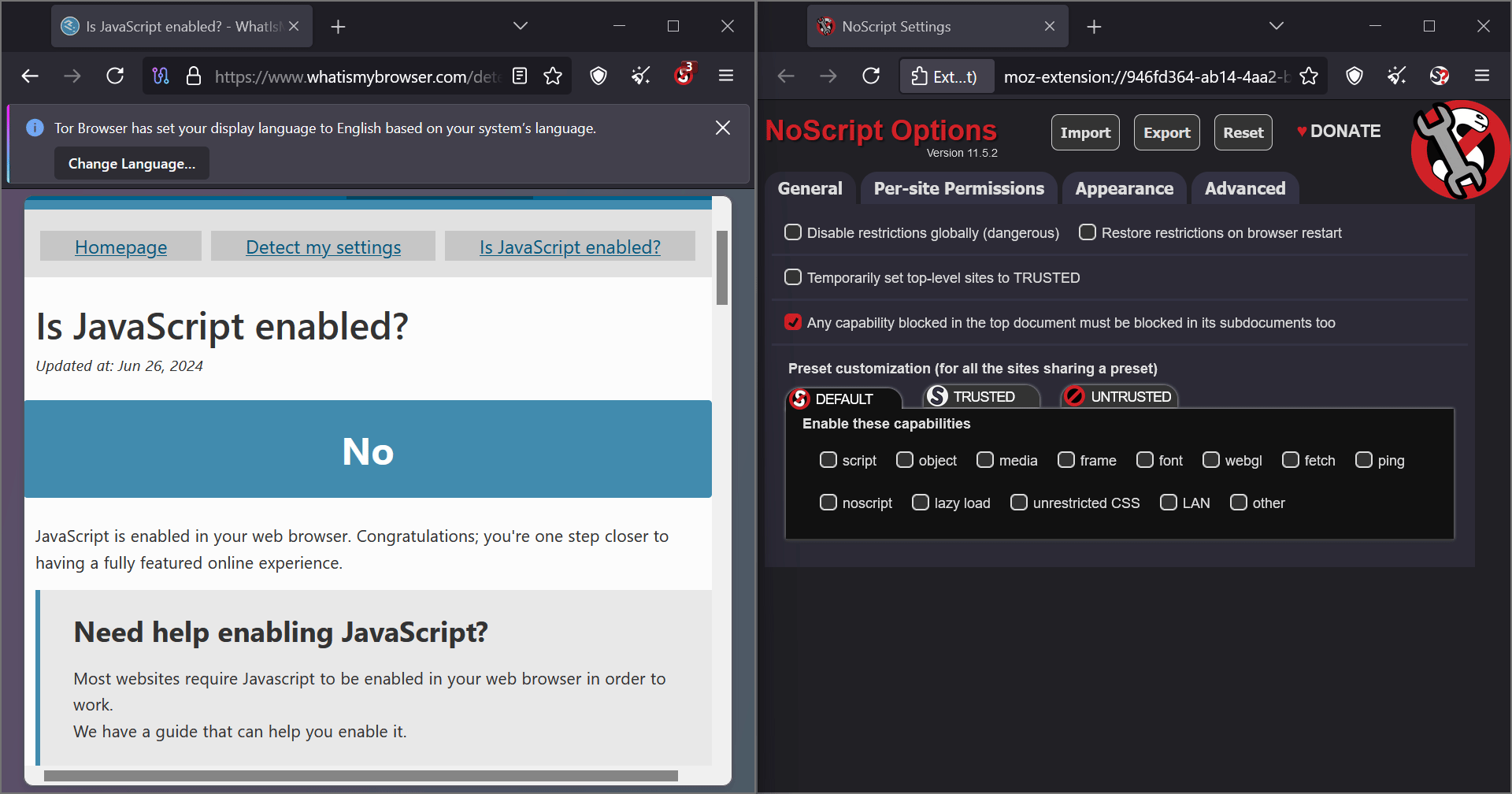
What does the “Override Tor Browser’s Security Level preset” checkmark do?
From my testing, it only enables additional settings to mark domains as trusted or untrusted. That’s it.
BTW you see, the website is still visible even after unchecking all the settings. I mentioned this this earlier.
Let’s say I visited a website, enabled the “Override” button, and set the domain to trusted. Then, I visit another website (or even stay on the same site), and as soon as I uncheck the “Override” button, shouldn’t it just revert back to the default settings? Why does it still stay on trusted? Is this expected behavior?
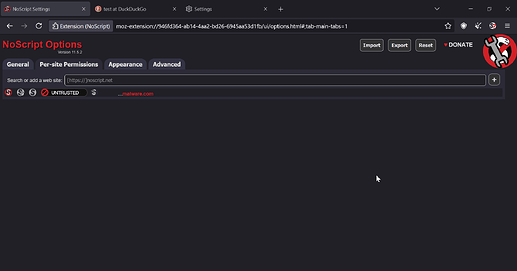
So let’s say I want to browse in a set where I disable everything by default, including on Default preset and Untrusted preset both. For example, I’d like to mark unsafe websites like malwaredotcom(just as an example here) as untrusted to not not load up anything from that domain. (By the way, as shown above with DuckDuckGo and that other website, some content still loads even in these scenarios in default mode with everything checked, and the same happens in untrusted mode with everything unchecked btw.)
Do I need to check the “Override settings” option to apply this setup? Or will it follow the standard settings preset? where NoScript and other elements are allowed to load by default? (For instance, “LAN” and some elements on untrusted sites are enabled)
From my understanding, the “Override settings” checkbox lets you create permanent rules for websites, such as marking them as trusted or untrusted through the NoScript add-on. That’s it—nothing more. right?
So, if I don’t create permanent rules (trusted or untrusted), it doesn’t matter whether the “Override” checkbox is ticked or not, right? It seems to function the same way regardless.
If I go into the add-on settings and create a rule marking malwaredotcom as untrusted, it doesn’t matter if the “Override” checkbox is enabled or not; the rule still applies, right?
So basically, the checkbox only allows you to create rules via the add-on settings. It doesn’t affect anything else, right?
What I am trying to do. Is this a safe approach? I was watching a video by someone on YouTube, and they suggested this setup, but I’m concerned it might make me stand out.
I’m also concerned about another issue. Let’s say I’m using the default strict mode or preset. Typically, some website functionality would still work by default, but in my case, nothing works at all. My first instinct would be to set things to ‘temporarily trusted,’ which would end up loading almost everything, creating a much bigger privacy concern, right?
I think in this situation, instead of resorting to ‘temporarily trusted,’ using the custom mode might be a better option right?. NoScript also highlights certain elements and enabling those should help make the website work without compromising privacy.
IDK, Please let me know, you guys, which setup I should continue with, but before I proceed, I want to fully understand everything first.
How to Unbreak Websites?
See this:
On “Safer” mode (Nothing changed with NoScript) websites work fine:
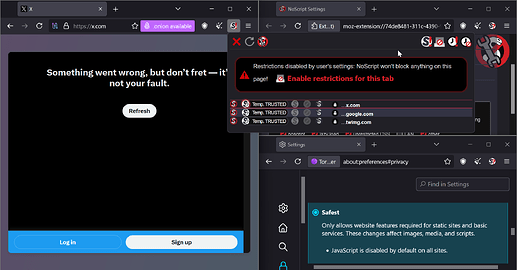
On “Safest” mode, ofc the sites would be broken but even after marking domains as temporarily trusted the website still doesn’t work:
Even setting them to “Temporarily Restricted” doesn’t work:
What is happening here? I do not understand the link between the privacy settings in Tor and NoScript.
Addons in Tor browser
Using uBlock Origin (uBO) in Tor
I am aware that it is not recommended to install filter-based extensions like uBO in Tor Browser. However, Tails OS includes uBO by default in their Tor Browser. Why is this the case? Should I disable uBO in Tails’ Tor Browser?
If there is no risk, should I install uBO in the regular Tor browser? If there is a risk, should I disable uBO in Tails Tor browser?
Other Extensions in Tor Browser
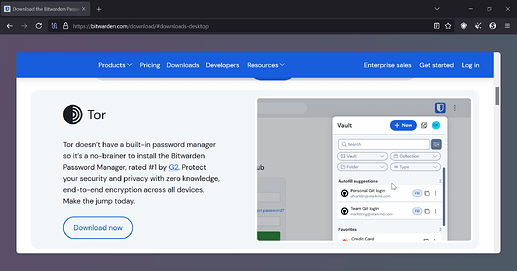
Can we use extensions like Bitwarden in Tor? Bitwarden’s website itself promotes its use in Tor:
ig it’s not mandatory to avoid installing addons, as there is logic behind. Can you provide scenarios and some addons where installing them is completely fine? Also, I like to know if use any addons in your Tor browser right now.