I can confirm. Using Tor nowadays is becoming meaningless because many website administrators block the IP addresses of Tor exit nodes.
A suggestion on how we can improve Tor architecture in order to bypass Tor blocks by destination websites.
My ideas may be kind of fundamental but I hope you will read it till the end.
I have been using Tor for several years and I’ve notice that Tor is becoming useless nowadays for browsing the Internet. But why is it like that? The main reason is that more and more destination websites are blocking Tor exit nodes so it is becoming impossible for Tor users to browse these sites at all. Some of websites are blocking access for Tor visitors at all, some of websites are blocking the ability to register accounts. For example, Instagram, Facebook, Telegram and so on have the built-in anti-spam AI systems which can detect the fact of using Tor and automatically block an ability to register new accounts through Tor exit nodes.
So, Tor is suitable for browsing the Internet in a read-only mode but it is absolutely useless if a user wants to actively use the Internet (register social media accounts, take part in discussions and so on).
Tor has an ability to hide the fact of its usage from the Internet Service Provider (ISP) by connecting to pluggable transports (such as obfs4, meek, webtunnel) but Tor has no feature to hide the fact of using Tor from destination websites.
Honestly speaking, this is not Tor-exclusive issue. I have been using Tor, VPNs, open proxies for many years and I can say that most of Tor exit nodes/VPNs/Proxies IP addresses have been already disclosed and they are all published in abusable IPs list (such as DroneBL database). It means that any destination website administrator can easily link a database with all abusable IPs to his web-server and block all incoming connections from both Tor exit nodes, VPNs and proxies IPs.
Well, Tor Project developers can say “It is not Tor problem, you should blame website administrators for blocking Tor”. But in fact, it is Tor problem. If we do nothing then we will make Tor absolutely useless in some years because most of website administrators have already banned Tor exit nodes.
What do users do nowadays to bypass Tor blocks by destination websites?
Users use complex software solutions like Whonix-Gateway and Whonix-Workstation which allows to use Tor in a combination with VPN or Socks proxy. Users use Whonix to build schemes like:
ISP → Tor entry node (or a obfuscated bridge) → Tor intermediate node → Tor exit node → OpenVPN (TCP) → Website
or
ISP → Tor entry node (or a obfuscated bridge) → Tor intermediate node → Tor exit node → Open Socks Proxy → Website
in order to bypass Tor restrictions by destination websites. However, this approach does not guarantee that website is not blocking the IP address of the VPN server or an Open Proxy server. Some of websites such as imageboards are aggresively blocking not only Tor exit nodes IPs but also VPNs/Proxies IPs using abusable IP database (like DroneBL and so on).
How can we solve this problem?
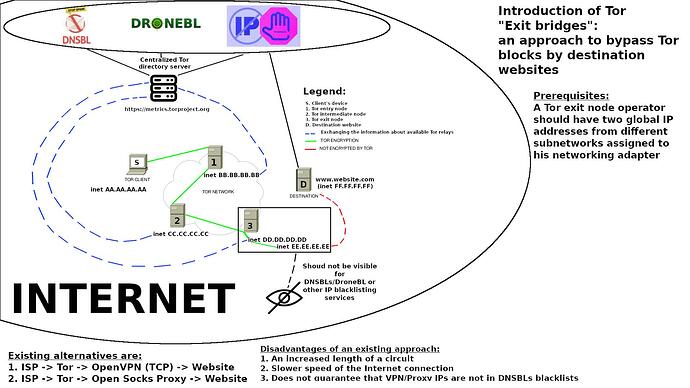
When I was seeking for public VPNs, I occasionally noticed that some of VPN administrators have two global IP addresses assigned to a one networking interface. One of these IP addresses (let it be CC.CC.CC.CC) is publicly available and used for connecting to a VPN and the other one (let it be DD.DD.DD.DD) is hidden to public and shown to a destination website only. The “DD.DD.DD.DD” address should not be presented in DroneBL or other abusable IPs databases. It means, when a user connects to a VPN with an IP address CC.CC.CC.CC (which will be included to abusable IPs list because it is publicly disclosed), then a VPN server is redirecting all the traffic (by its internal rules, let it be IPtables firewall) from CC.CC.CC.CC to DD.DD.DD.DD (which is not in abusable IPs list because it has never been published on the Web) and then sends the traffic to the destination website. This approach allows users to bypass automatic anti-spam systems from many websites and allows users to browse the Internet freely.
A purposed architecture
Let’s assume that
AA.AA.AA.AA
BB.BB.BB.BB
CC.CC.CC.CC
DD.DD.DD.DD
Are global IPv4 addresses (0-255.0-255.0-255.0-255).
AA.AA.AA.AA, BB.BB.BB.BB, CC.CC.CC.CC are publicly disclosed IPv4 addresses of Tor relays (entry, intermediate and exit one).
DD.DD.DD.DD is a hidden exit IPv4 address for Tor exit node which should not be published or disclosed on Web.
ISP → Tor entry node (inet AA.AA.AA.AA) → Tor intermediate node (inet BB.BB.BB.BB) → Tor exit node (two IPs on one networking interface: CC.CC.CC.CC and DD.DD.DD.DD) → Website
I hope this architecture will be implemented in future Tor releases. Thank you!
Here you can see a purposed architecture of Tor “Exit bridges”: an idea on how to bypass Tor blocks by destination websites: