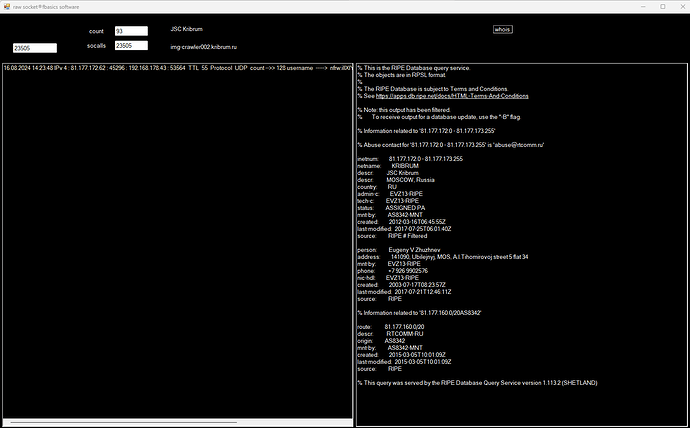
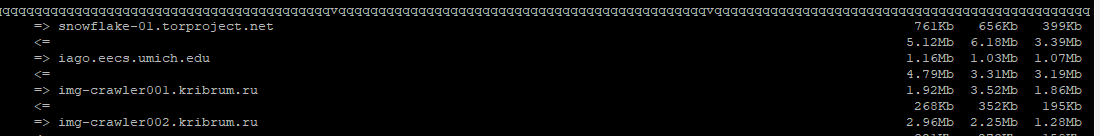Hi guys, I occasionally take a look at the users who connect via my snowflake in the Edge browser. Most of them are users from Iran and Russia. Today I discovered a web address of the Russian site called Kribrum ru. This was the first site that did not point to an individual user but to a company. I have no idea what it means, perhaps it is even uncritical, hence my question whether anyone knows this site or even knows more about the company. I have switched off snowflake for now.
@ekkcodeer, I am not sure how you are getting this info. Snowflake doesn’t work this way.
ref. https://snowflake.torproject.org/
There is no need to worry about which websites people are accessing through your Snowflake proxy. Their visible browsing IP address will match their Tor exit node, not yours.
I don’t think you can see which sites are visited. Those russian site/company is from other plugin ![]()
user → snowflake proxy (your mozzila) → tor entry → tor middle → tor exit → website
Only tor exist can see the exit but doesn’t know client IP.
@ekkcodeer, Tor is for everyone. It does not matter who connects to your proxy. Except for cases of DDoS attack, but even that is a reason to add bans to firewall and not to “switch off snowflake”.
I think this is saying he can see who is connected to his machine and not the site visited. The image looks like a netstat or tcpview output.
I can see this if I use the debugging option in Firefox.
It looks something like this:
a=candidate:2218299339 1 udp 1694498815 x.xx.xx.xx 47226 typ srflx raddr 0.0.0.0 rport 47226 where x.xx.xx.xx is the IP address
It’s all encrypted UDP packets.
See this thread where we discuss this A follow up question about Snowflake
I looked at their website. They claim to do internet data gathering and analysis, funded by grants from the Russian government. Checks out.
How do you know that this is related to Snowflake though?
It is uncritical enough not to turn off Snowflake because of this.
About whether it is ethical to post the info about who connects to your Snowflake: I think it’s OK in this case. They’re watching us, we’re watching them.
It was resmon but it could have been tcpview too … I usually use wireshark
you mean that kribrum.ru would operate a Tor exit node in Russia, which I now see in my connection … ?
kk … turned it on again … I just didn’t want to give the evil ruzzen a chance to try something … irony off
Well that’s wrong … proven by Snowflake
Yes i wanted to say users and I have typed sites, don’t know why, and completely forgot about netstat, my mistakes ![]()
iago.eecs.umich.edu is the same with snowflake-02.torproject.net so that connection is legit.
Regarding the 2nd IP, maybe someone who is working at kribrum wanted to browse the free internet from work, or maybe that company tools are not working because of restrictions and they use snowflake like other users to browse free internet, what’s the problem?
broker address
A username looks like this
username -----> J/br:vRLUeUFASSzVopJS
It is cryptic and randomly generated
simply watch your net traffic stun activities
To be precise, it’s the Snowflake server (bridge / relay).
I mean, for that particular connection how did you figure it out? That it correlated timing-wise with STUN activity?
I haven’t looked at the whole thing from the perspective of the snowflake coding (I don’t know anything about the Go stuff) but by simply observing. It doesn’t seem to be part of the snowflake code but rather based on a peculiarity of WebRTC to use STUN. It is only visible if you are behind a NAT. My little program shows it like this.
Ah … ok … I see I still have a lot to learn in order to understand and monitor the whole system … So I can still incorporate a lot into my work and progress project which I will put online on a small website and occasionally develop further … the snowflake monitor is on cvision.lima-city.de … observers are welcome
So this kribrum are bots that are crwaling the internet via Snowflake because clear net is banned in Russia
They even have a YouTube channel
Channel info
The channel of the company Kribrum, which is the leading russian system for monitoring and analyzing the content of social networks.
One video is titled
Destructive groups in social networks during distance learning
It all looks like russian propaganda channel … why should they use crawler bots via snowflake to reach clear net ?
And everything takes place in public
all looks … mmh … let’s say strange ?
Okay maybe it’s a bit off topic …
Interesting idea.
Though I should mention that from some Russian VPS / VDS providers you can still access Tor directly.
For government-loyal providers, the system will certainly be able to leave one or two doors open so that they certainly don’t have to use Tor or other means to access the internet. If such people use Tor or Snowflake, then they want to find out something about the function of bypass systems