Hello,
If someone has the IP address and port of my Tor server, they can connect to it and get services.
How can I authenticate it?
Thank you.
Hello,
If someone has the IP address and port of my Tor server, they can connect to it and get services.
How can I authenticate it?
Thank you.
Hello,
Thank you so much for your reply.
Isn’t there something simpler like setting the username and password?
I think the simplest solution would be to setup a Onionshare (see: How OnionShare Works — OnionShare 2.6 documentation)
Hello,
Thanks again.
Please see the following image that I found via Google search:
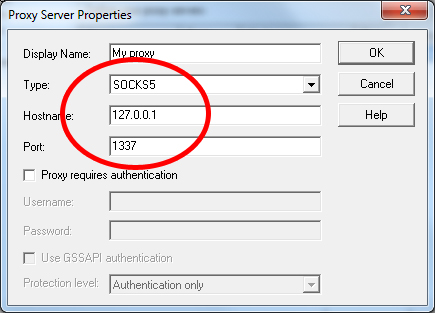
As you see, it has a Proxy require authentication option. The client must enter the username and password for using the proxy.
I want when someone enters the IP address of my Tor server to his\her browser proxy section to use it as a proxy server, then he\she must enter the username and password to use.
I believe the question is about limiting access to a Tor bridge (relay?), not an Onion service. With that said, firstly, I don’t know a direct solution, but:
BridgeDistribution is none.Hello,
Thank you so much for your reply.
Consider a company that lunched a Tor server and by default if anyone enters the Tor server IP address and port, then he\she can use the proxy. I want to limit it.
Hello,
How about the following lines?
Socks5ProxyUsername username
Socks5ProxyPassword password
Socks5Proxy host[:port]
Tor will make all OR connections through the SOCKS 5 proxy at host:port (or host:1080 if port is not specified).
Socks5ProxyUsername username
Socks5ProxyPassword password
If defined, authenticate to the SOCKS 5 server using username and password in accordance to RFC 1929. Both username and password must be between 1 and 255 characters.
These are used, when your Tor needs to connect through a proxy to reach the internet - not for Tor to provide a SOCKS-proxy.
Hello,
Thank you for your reply.
Why did the Tor not consider such a feature?