Hello all, i’m trying to make a quality post so please bear with me.
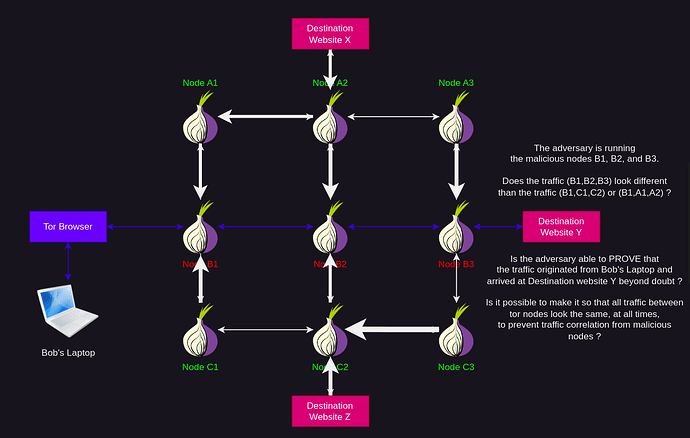
Let’s assume that you are currently accessing website Y via the Tor browser, and that you just so happened to get a circuit going through 3 malicious tor nodes. What then ?
The adversary is running the malicious nodes B1, B2, and B3.
Does the traffic (B1,B2,B3) look different than the traffic (B1,C1,C2) or (B1,A1,A2) ?
Is the adversary able to PROVE that the traffic originated from Bob’s Laptop and arrived at Destination website Y beyond doubt ? Because if this the case right now, i genuinely believe that this shouldn’t be tolerated and put on the Tor roadmap. ALL traffic that comes and goes from tor nodes should have the same packet size more or less, to make sure that the adversary can’t tell where any particular connection is coming from and going. They must all blend together and look the same from the adversary’s perspective. There should be decoy traffic being sent around.
I highly suggest reading on what nym is trying to achieve Mixnet and mullvadvpn’s DAITA implementation DAITA: Defense Against AI-guided Traffic Analysis , which is aimed at just that, to make sure that the connections look the same.
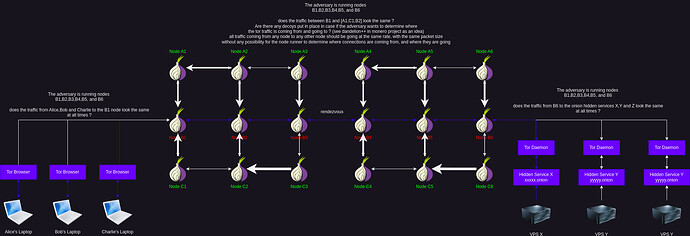
Is it possible to make it so that all traffic between tor nodes look the same, at all times, to prevent traffic correlation from malicious nodes ? Is this already planned ? If it is not planned yet, can this be put on the roadmap ?
This is the main criticism i have on Tor (despite how much i respect the project), it shouldn’t matter who runs tor nodes to the users, as they shouldn’t be able to correlate any user’s traffic to any other users’ traffic