My relay is rejecting a lot of these for some reason.
It looks like new form of (D)DoS.
This night I noticed spike of CPU usage on my relay.
But worse than that, RAM consumption of Tor process increased (~0.5 GB → ~1.9 GB) and did not lowered after CPU load lowered to usual levels.
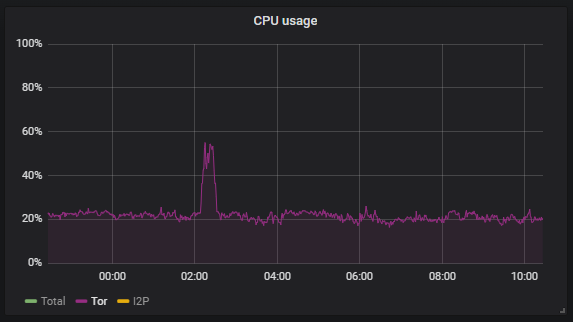
Also I noticed change of INTRODUCE2 rejected count around the same time:
Nov 16 02:05:32.000 [notice] Heartbeat: Tor's uptime is 11 days 11:59 hours, with 7811 circuits open. I've sent 910.77 GB and received 878.87 GB. I've received 706124 connections on IPv4 and 3532 on IPv6. I've made 408667 connections with IPv4 and 0 with IPv6.
Nov 16 02:05:32.000 [notice] While not bootstrapping, fetched this many bytes: 233777140 (server descriptor fetch); 8520 (server descriptor upload); 14195217 (consensus network-status fetch); 5290968 (microdescriptor fetch)
Nov 16 02:05:32.000 [notice] Circuit handshake stats since last time: 11/11 TAP, 203200/203200 NTor.
Nov 16 02:05:32.000 [notice] Since startup we initiated 0 and received 0 v1 connections; initiated 0 and received 0 v2 connections; initiated 0 and received 24589 v3 connections; initiated 0 and received 352615 v4 connections; initiated 355997 and received 308731 v5 connections.
Nov 16 02:05:32.000 [notice] Heartbeat: DoS mitigation since startup: 8 circuits killed with too many cells, 79545 circuits rejected, 46 marked addresses, 0 marked addresses for max queue, 0 same address concurrent connections rejected, 0 connections rejected, 13 single hop clients refused, 0 INTRODUCE2 rejected.
Nov 16 08:05:32.000 [notice] Heartbeat: Tor's uptime is 11 days 17:59 hours, with 7716 circuits open. I've sent 933.66 GB and received 902.15 GB. I've received 730283 connections on IPv4 and 3598 on IPv6. I've made 415067 connections with IPv4 and 0 with IPv6.
Nov 16 08:05:32.000 [notice] While not bootstrapping, fetched this many bytes: 239561620 (server descriptor fetch); 8520 (server descriptor upload); 14551857 (consensus network-status fetch); 5364518 (microdescriptor fetch)
Nov 16 08:05:32.000 [notice] Circuit handshake stats since last time: 2382198/2382198 TAP, 292331/292331 NTor.
Nov 16 08:05:32.000 [notice] Since startup we initiated 0 and received 0 v1 connections; initiated 0 and received 0 v2 connections; initiated 0 and received 29776 v3 connections; initiated 0 and received 361320 v4 connections; initiated 361299 and received 318821 v5 connections.
Nov 16 08:05:32.000 [notice] Heartbeat: DoS mitigation since startup: 8 circuits killed with too many cells, 87689 circuits rejected, 47 marked addresses, 0 marked addresses for max queue, 35 same address concurrent connections rejected, 0 connections rejected, 13 single hop clients refused, 7294 INTRODUCE2 rejected.
I thought so. I wasn’t getting these before but now I am. I still have plenty of CPU and RAM though.
I have just started seeing this on relays. Interestingly on each relay the number is remarkably consistent. On one relay it is exactly 21313 every DoS cycle (4 hours). On another it started off as 33 every four hours for 4 cycles and has just jumped to 25512.
As I understand it, this is the message which facilitates tor client and tor hidden service meetings.
It makes me wonder if it’s an attempt at flushing out the location of a hidden service more than an actual denial of service attempt. A DoS where you don’t actually deny anything is not worth the time it takes to modify the tor server software. It makes me think this is more an attempt at using a combination of pings and traffic correlation to de-anonymize a hidden service.
Note since startup text in that message.
It’s a type of “attack”. If i remember correctly when i had read about it in discussion of a bug ticket, the team said that nothing can be done about it at least from a firewall standpoint, and the relay will handle it to filter it out.
Might be my idea, but your rejected circuit count (typical DDOS attack marker) seems a little high for its related uptime. I’d be more concerned about that. ![]()
Intresting I didn’t know what it was but you’re right about it relating to hidden services (http://i3xi5qxvbrngh3g6o7czwjfxwjzigook7zxzjmgwg5b7xnjcn5hzciad.onion/rend-spec/introduction-protocol.html) Clearnet (The introduction protocol [INTRO-PROTOCOL] - Tor Specifications).I was not getting these before it started recently. I Guess I can’t do anything about it. I’ll just keep monitoring.
Update: node went down and I re-started it. There is no INTRODUCE2 connections rejected today. Looks like it was an attack on hidden services.
This topic was automatically closed 24 hours after the last reply. New replies are no longer allowed.