TLDR
A small-scale amateur experiment was conducted to assess the impact of uBlock Origin and Privacy Badger on the Tor Browser’s fingerprint size and uniqueness. Measurements were taken using six different devices (two desktops, two laptops, two phones) across three security settings (“standard,” “safer,” and “safest”), with and without Tails (on devices that could support it). Browser fingerprints were recorded using the EFF’s Cover Your Tracks tool.
Key Findings
-
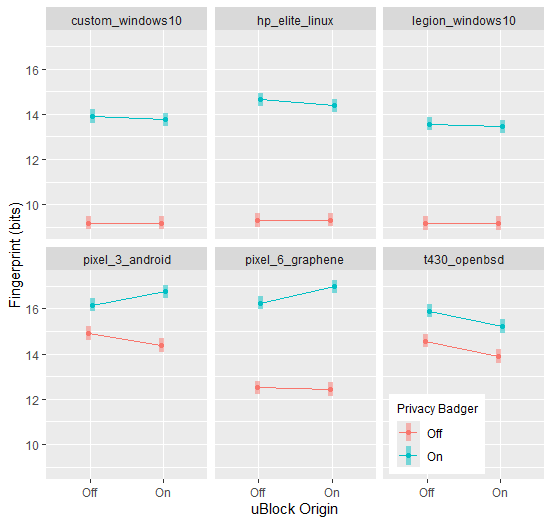
uBlock Origin resulted in a slight reduction in fingerprint size on some devices when used by itself. However, when combined with Privacy Badger, it resulted in larger fingerprint sizes on the two mobile devices.
-
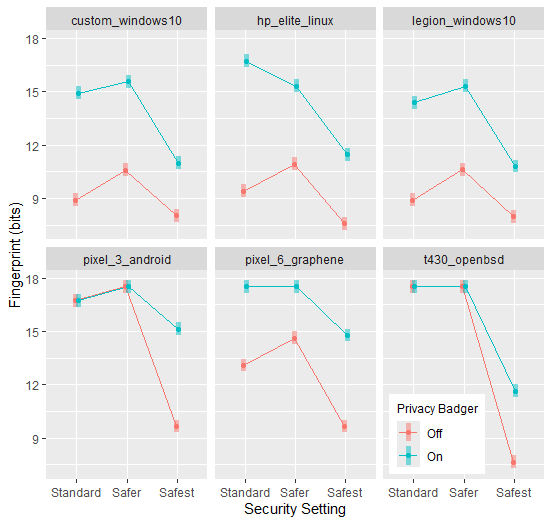
Privacy Badger was associated with a large increase in fingerprint size across systems and security settings.
-
The “safest” security setting resulted in the smallest fingerprints, whereas the “safer” setting often resulted in larger fingerprints compared to the “standard” setting.
-
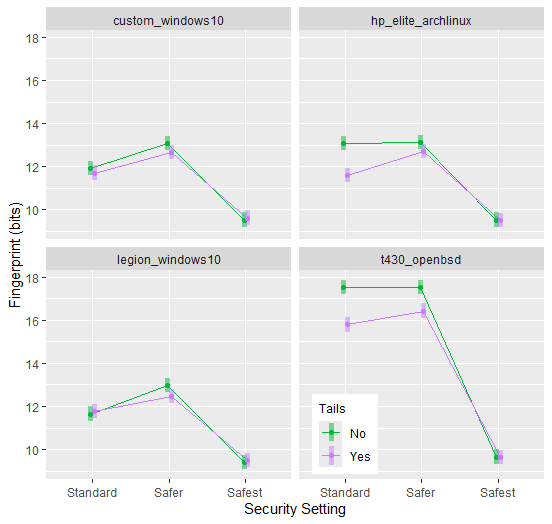
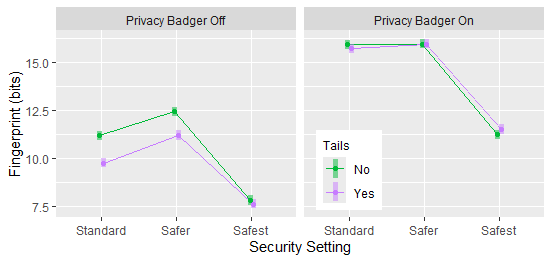
Tails was associated with a reduction in fingerprint size for “standard” and “safer” security settings, but this benefit did not persist when Privacy Badger was installed and enabled.
-
8% of the tested configurations produced a unique fingerprint, all occurring with the “standard” and “safer” security settings and primarily involving Privacy Badger.
-
It is possible to create a unique fingerprint while using Tails at lower security settings by installing and enabling Privacy Badger.
-
Older or uncommon hardware may contribute to larger or unique fingerprints.
-
The mobile devices tended to have larger fingerprints than the desktops and laptops, even under the “safest” security setting, but further investigation is needed to confirm this pattern.
Unofficial Tentative Recommendations
-
It is probably OK to use uBlock Origin by itself. It may even result in a smaller fingerprint in addition to blocking ads.
-
Do not install any other add-ons beyond uBlock.
-
Use only the “safest” security setting if possible.
-
If you anticipate having to use a lower security setting for website functionality, use Tails on commonplace hardware.
-
Use a desktop or laptop instead of a phone, if possible.
Introduction
Whether to use additional privacy and security add-ons with the Tor Browser is a perennial question [1] [2] [3] [4] [5] [6] [7].
On its face, it seems reasonable to assume that additional blockers could only improve anonymity. After all, Tails itself ships with uBlock Origin pre-installed. On the other hand, the Tor Project warns that additional add-ons can create a unique device fingerprint that can allow you to be tracked [8] [9]. An analogy might be a spy wearing three disguises at the same time. Maybe their true identity is unknown, but as the only person wearing three sets of clothes simultaneously, they are easily identified wherever they go.
The official recommendation of the Tor Project is to use the Tor Browser without any additional add-ons [10].
I have read a lot of discussion and speculation, but I have not seen any actual data, so I decided to run a home-brew experiment to inform my own operational security. The goal was to explore the effect of additional privacy add-ons on the Tor Browser’s fingerprint under different security settings, for different base systems, with and without using Tails.
Methods
I took a convenience sample of 6 devices: two desktops – an HP EliteDesk running Linux 6.13.5 (I use Arch, btw) and a custom gaming rig running Windows 10, two laptops – a Lenovo T430 running OpenBSD 7.7 beta and a Lenovo Legion 5 running Windows 10, and two phones – a Pixel 3a running stock Android 12 and a Pixel 6a running Graphene 2025031400.
Browser fingerprint was measured using Cover Your Tracks, a tool from the Electronic Frontier Foundation (EFF) that fingerprints your browser and reports the sample proportion of other visitors that share the same fingerprint and its information content in bits. It also tells you if your fingerprint is unique (the only one it has seen). Information was apparently capped at about 18 bits due to their own limited sample size of about 260,000 visitors. I left the “Test with a real tracking company” box unchecked.
The add-ons tested were uBlock Origin and Privacy Badger. The latter was developed by the EFF to block advertisements and tracking cookies that do not respect the Do Not Track setting [11]. NoScript was enabled with default settings for every trial and I did not mess with it.
The browser fingerprint (in bits) and its uniqueness (0,1) were measured for every possible combination of add-on (none, uBlock Origin, Privacy Badger, both) and security setting (standard, safer, safest), on every base system with and without using Tails (when possible). After every measurement, I clicked the “New Identity” button to restart the browser. The total number of observations was n=144.
Linear models were fit with the lm function in R. To prevent overfitting, stepwise variable selection was done in both directions with stepAIC. Model diagnostics were assessed visually. Statistical significance was taken to be p < 0.05. Post hoc comparisons were done using Tukey adjustments.
Results
I will try to state only the statistically significant results in a qualitative way without getting bogged down in the numbers.
Use of add-ons
Privacy Badger was associated with a large increase in average fingerprint, varying across systems.
In contrast, uBlock was associated with a small reduction in fingerprint for the T430 when Privacy Badger was both off and on. For the two mobile devices, uBlock was associated with a small reduction in fingerprint when Privacy Badger was off, but a small increase when Privacy Badger was on. The slight fingerprint reductions seen with the other laptops and desktops were not statistically significant.
The “safer” setting was associated with a larger browser fingerprint compared to the “standard” setting in all configurations except the T430, and the HP Elite and Pixel 6 with Privacy Badger on. The “safest” setting resulted in the lowest fingerprints. The two mobile devices had larger fingerprints compared to the other systems on the “safest” security setting.
Use of Tails
Using Tails was associated with a small reduction in browser fingerprint, but only with the “standard” and “safer” settings. The largest reductions were at both the “standard” and “safer” settings of the HP Elite and the T430, with smaller reductions in the “safer” setting with the custom desktop and Legion 5 laptop. At the “safest” security setting, there was no difference between using Tails vs. the original operating system.
The fingerprint-reducing effect of using Tails at lower security settings did not persist when Privacy Badger was installed and enabled.
Unique fingerprints
Twelve of the 144 configurations (8.3%) resulted in a unique browser fingerprint. All of these occurred while using the “standard” or “safer” setting. All but three occurred while using Privacy Badger by itself. The other three occurred while using uBlock and Privacy Badger together (but only on the mobile devices). In no cases did a unique fingerprint result from using uBlock alone or while using the “safest” security setting.
Three unique fingerprints (2.1%) happened when using Tails: on the custom desktop and on the T430, in both the “standard” and “safer” settings, with Privacy Badger enabled and uBlock disabled.
Table 1
| Form Factor | base system | Tails | Security Setting | uBlock Origin | Privacy Badger | Fingerprint (bits) |
|---|---|---|---|---|---|---|
| Desktop | Custom Windows 10 | 0 | 0 | 0 | 1 | 15.02 |
| Desktop | Custom Windows 10 | 1 | 1 | 0 | 1 | 16.02 |
| Laptop | T430 OpenBSD | 0 | 0 | 0 | 0 | 18.02 |
| Laptop | T430 OpenBSD | 0 | 0 | 0 | 1 | 18.02 |
| Laptop | T430 OpenBSD | 0 | 1 | 0 | 0 | 18.02 |
| Laptop | T430 OpenBSD | 0 | 1 | 0 | 1 | 18.02 |
| Laptop | T430 OpenBSD | 1 | 0 | 0 | 1 | 18.02 |
| Laptop | T430 OpenBSD | 1 | 1 | 0 | 1 | 18.02 |
| Mobile | Nexus 3 Android | 0 | 1 | 0 | 0 | 18.03 |
| Mobile | Nexus 3 Android | 0 | 1 | 1 | 1 | 18.03 |
| Mobile | Nexus 6 Graphene | 0 | 0 | 1 | 1 | 18.03 |
| Mobile | Nexus 6 Graphene | 0 | 1 | 1 | 1 | 18.03 |
Discussion
The results suggest that using uBlock by itself has no effect or may slightly reduce the fingerprint (Figure 1). However, when used with Privacy Badger (and possibly other add-ons) it may contribute to a larger browser fingerprint and even a unique fingerprint on some systems (Figure 1, Table 1).
In this experiment, there was no advantage to using Privacy Badger (at least in terms of fingerprint reduction). On every system and security setting it resulted in a larger fingerprint or at best no change (Figure 2). It also negated the benefit of using Tails (Figure 4). This may hold true for other add-ons as well, or it may not.
The “safest” security setting resulted in the smallest fingerprints (Figures 2, 3, 4). In most cases (but not all), the “safer” setting actually resulted in a larger fingerprint compared to the “standard” setting. However, there may be other advantages to using “safer” over “standard” beyond just fingerprinting, but that is beyond the scope of this experiment.
The underlying hardware may have a greater effect on fingerprint than the operating system. For example, the use of Tails was able to reduce the browser fingerprint of the T430 in the lower-security settings (Figure 4, bottom-right), but that machine still had the largest fingerprint. A closer look at the detailed results of the test showed that “screen size and color depth” was the largest contributor to its fingerprint. The T430 is 13 years old and has a 14" screen with a resolution of 1366 x 768. There probably are not many still in use, so maybe it should come as no surprise that such a dinosaur had a unique fingerprint. This could underscore the importance of using commonplace hardware especially if you anticipate having to use a lower security setting.
This experiment also demonstrated that it is possible to have a unique fingerprint using Tails on some systems by installing additional add-ons (Table 1). However, this only occurred in the “standard” and “safer” security settings when uBlock had been disabled. Whether it is always necessary to disable uBlock and use a lower security setting for this to occur is not clear, though (see the Limitations section).
It also may be important to note that the two android devices had larger fingerprints compared to the desktops and laptops on the “safest” security setting (Figure 2). The Pixel 3 had a unique fingerprint in the “safer” security setting even without installing any additional add-ons. It may be because these two phones are relatively old and are probably uncommon in the wild, or it may be due to differences in the desktop vs. Android versions of the Tor Browser, or it may be a coincidence.
Limitations
A major limitation was the small sample size of the experiment. Only six systems were tested. Most of the hardware was relatively old, and no Apple devices were tested. Therefore, the sample should not be considered representative of the population of base systems out there, and any extrapolations or generalizations beyond the limited scope of this experiment should be done cautiously.
Another limitation is that I did not randomize the order in which configurations were tested. Each sequence on a particular system and security setting began with no addons enabled and ended with both uBlock and Privacy Badger enabled. This may have introduced a bias, as Cover Your Tracks may update its database in real-time. If an early test produced a unique fingerprint, subsequent configurations could appear less unique – not because of an actual change in fingerprint size but due to prior observations in the dataset that I myself introduced.
Conclusions and personal recommendations
I hesitate to give other people advice, but for my own self I feel comfortable making the following recommendations:
-
It is probably OK to use uBlock Origin by itself. It may even result in a smaller fingerprint in addition to blocking ads.
-
Do not install any other addons beyond uBlock.
-
Use the “safest” security setting if possible.
-
If you anticipate having to use a lower security setting for website functionality, use Tails on commonplace hardware.
-
Use a desktop or laptop instead of a phone, if possible.