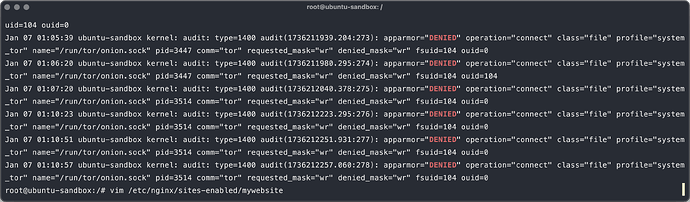
I am not sure that it is the right place to post about this problem, please tell me, if I am wrong.
Torproject.org suggests using unix sockets to connect Tor and Nginx:
HiddenServiceDir /var/lib/tor/my-website/
HiddenServicePort 80 unix:/var/run/tor/my-website.sock
However, some Ubuntu users struggle with these settings: case 1, case 2
After spending two hours with ChatGPT, I think I’ve found the cause of the problem.
By default, AppArmor prevents Tor from writing to the socket placed in /run/tor. To resolve this, move the socket to another location, such as /var/lib/tor/my_website/onion.sock.
Here’s the updated nginx configuration:
server {
listen unix:/var/lib/tor/my_website/onion.sock;
<…>
}
Here’s the updated torrc:
HiddenServiceDir /var/lib/tor/my_website/
HiddenServicePort 80 unix:/var/lib/tor/my_website/onion.sock
To ensure proper permissions, use the following commands:
chown debian-tor:debian-tor /var/lib/tor/my_website/onion.sock
chmod 660 /var/lib/tor/my_website/onion.sock
These settings allow Tor to work with unix sockets on Ubuntu. While user-level apparmor changes may be possible, I don’t see the advantages.
I hope to save time for future Onion Service operators. Perhaps someone will also consider fixing the manual on torproject.org.
For enthusiasts, an interesting read about the decision to revert to the original socket placement is: