Is connecting to all available bridges like this a good idea for censored users?
I just wanted to ask, I’ll delete all these bridges after posting this.
Is connecting to all available bridges like this a good idea for censored users?
Update: I think this is a waste of my time, and yours, if you want to try this. I connected to a onion website and it shows this:
It’s pointless if it can’t switch between bridges!
I believe Tor chooses bridges at random (or in sequence?) until it finds one that works. I’m not sure if there is rotation, like with Guard relays.
Anyway, I’m not sure what your point is? I think it’s ok to have backup bridges in case some one stops working.
If my point isn’t clear, let me state it.
I think Tor should allow bridge rotation between bridges of different protocols so that the chances that you’ll be able to make a successful connection (i.e, access the desired website) increases dramatically.
By this you mean “different kinds of bridges: obfs4, Snowflake, Conjure, WebTunnel”, right?
Bridges don’t have much to do with connecting to a website, because the connection to a website is performed by exit nodes of the Tor network, which don’t care what kind of bridge you’re using. The Tor network being used is the same for all different kinds of bridges. A bridge is just the entry node (the first out of three) of your circuit.
Tor does not choose configured bridges randomly or connect to them in sequence. What happens is a bit more complicated. The tor client will currently attempt to connect to all configured bridges simultaneously in order to fetch the bridge descriptors. This is definitely not ideal, and there’s an open issue on the subject if you’re curious about the ongoing discussions on this topic: Let bridge users choose to only reach their first working bridge (#40578) · Issues · The Tor Project / Core / Tor · GitLab
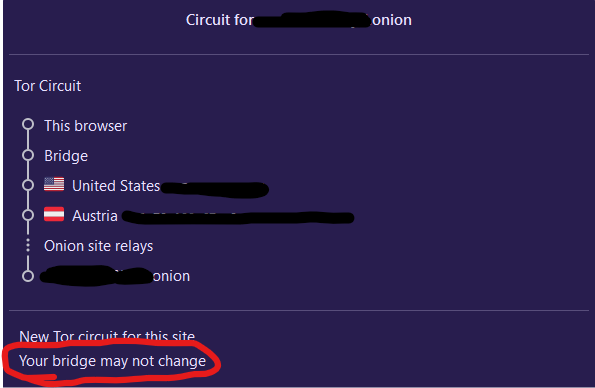
It’s pointless if it can’t switch between bridges!
The message “Your bridge may not change” does not mean it will never change. If you have multiple configured bridges and one bridge becomes unreachable, your tor client will start using a different bridge. The message here is only there to indicate that if you build a new Tor circuit for that site, there’s a chance that you’ll end up using the same bridge.
As to whether configuring multiple bridges is a good idea, it depends. Configuring more than one bridge is generally not harmful and it is useful for resiliency reasons as mentioned above. If one bridge is down or has been blocked, then it’s useful to have other bridges already configured. If you have too many, say 50, bridges, your client is going to make 50 connections at startup which is probably going to result in some network slowness while these connections are happening.
Specifically, what you’ve done above is to configure multiple different types of transports (snowflake, conjure, obfs4, meek, and webtunnel). This isn’t necessarily harmful, though it is very loud in the sense that if any of these circumvention methods are known to a censor and watched for, it will be more obvious that your client is connecting to circumvention tools. However, we don’t have a lot of evidence of that happening and the bigger problem I see with this is that the connection won’t be very efficient. The tor client is not smart about which bridge it ends up choosing and some bridges like the meek bridge are much slower than most obfs4 bridges. So I would recommend only configuring a few (3-5) bridges of a transport type you know works.