had slightly fewer ‘Bits of identifying information’.
entropy figures from test sites are nonsense. The data is tainted beyond anything meaningful
Here is an example
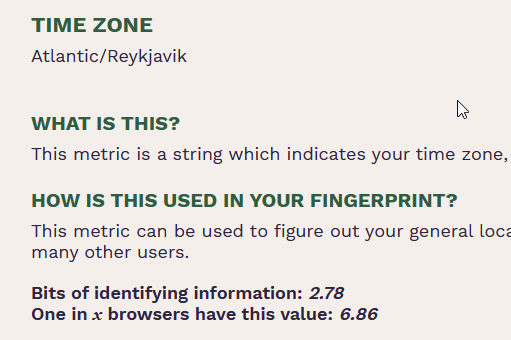
back of the napkin math
1 in 6.86 people are in timezone Atlantic/Reykjavik (from cover your tracks) - which is absolute garbage. Whilst population is not a perfect metric vs internet usage, 400k people live in Iceland. If that’s 1 in 6.86 then the world’s population is 2.75 million - which is about 2900 times difference. (2.9k x 2.75mn ~8 billion)
Even if we said half the world’s population had none or negligible internet usage, and that ALL of Iceland did (including all the babies at six weeks old with their ipads), and they had a 100k tourists at any given time with their devices automatically changed to the local timezone… it would still be well over a 1000 times difference
Here’s Icelandic as a language - again, not perfect, not everyone in Iceland will use is as their default web content language. But people outside of Iceland using Atlantic/Reykjavikwould be next to zero given the world’s internet population.
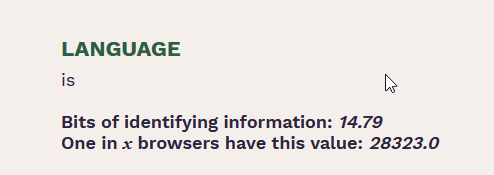
Also that figure is somewhat misleading, as it’s most likely under represented given all the users constantly testing and inflating en-US
So the site’s own data is telling you that 28323/6.86 is 4000+ times out of whack (but there’s a twist to this).
Iceland’s population (400k) is 0.005%, i.e 1/200th of 1%, of 8 billion. It’s a rounding error. Which, all things being equal, would make it’s timezone about 1 in 20k. At best (exclude half the world for being internet poor), it would be 1 in 10k of the internet population.
However, this is the timezone that TB uses, and TB has around 6mn users (I think, we’ll just roll with that). This barely moves the needle - 6.4mn/8bn is 0.08%
All this is just some back of the napkin math. The point is that the figures are tainted by small datasets, and repeated testing by users. The fact that TB and RFP’s timezone is so wildly overinflated proves this
The only way to get any idea of actual entropy is via studies/surveys where only one fingerprint per profile is collected.
Otherwise, if you’re not a FPing expert, do you even know what is being tested, if the test is any good, if something is actually equivalency and not entropy, and so on. In actual fact, the test has hardcoded biases for Brave (not Brave’s fault) to return better results in it’s summary simply on the basis of the number of randomized items. Which is not explained. In reality it means nothing, as all randomizing can be detected (as proven by the site itself) and the real purpose of antu-FPing is to protect the real value. So Brave get a massive thumbs up and Tor Browser gets pooped on.
The EFF has a lot to answer for pushing this entropy nonsense

