Introduction:
Hello everyone, this post has been in the works for a long time. I am making this post to:
- Consolidate everything that has happened over the lifetime of this thread.
- Bring new users and busy developers up to speed on the issue.
- Provide workarounds for the changes covered in “Summarized Timeline”. (not recommended)
After quietly observing what others have said about this issue, I have realized that everyone, regardless of if they are for or against a change to the 14.5.4 security level, has a fair point and raises valid concerns. As a result, I think that solutions which make the largest amount of users happy from both a usability and security standpoint while being the most simple to implement are the best to focus on currently.
This post is also meant to be the beginning of pivoting the focus of this thread to move from describing problems to discussing potential solutions and working out which one would be good. I might be too early, but I think this is where others would like to take it also.
Unfortunately, I’m in the dark as to if one of the solutions listed in this thread was favored by the developers or not, at the time of this post the Gitlab issue is marked as “To do” and I don’t know if there was any internal discussions or not.
Summarized Timeline:
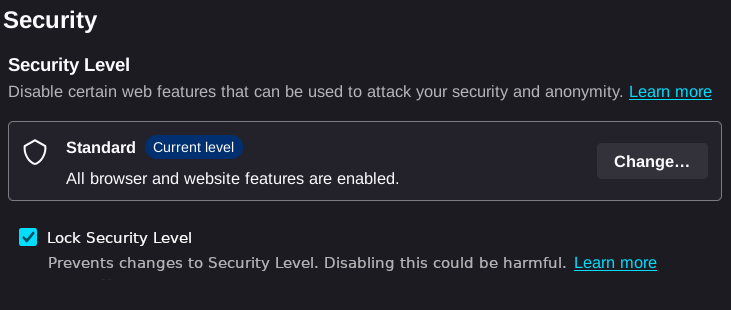
Changes were made to the SecurityLevel module starting in Tor Browser version 14.5.4. The major changes which affect users are the locking of the security state of Tor Browser upon starting it, and changing the security setting requires a restart for the browser.
This change is beneficial to users as the Tor Browser seemed to not entirely change all security parameters when switching security modes. A restart makes sure all security parameters are properly set. If you would like to replicate what @jonah’s covered, jonah’s article about this issue is at: https://www.privacyguides.org/articles/2025/05/02/tor-security-slider-flaw/.
Problems:
The current Gitlab issue for this post is Gitlab issue 43922.
Functionality Problems:
Most functionality problems reported in this thread by users revolve around not being able to temporarily enable JavaScript, the situations described so far are as such:
JS Related Issues:
- Can’t solve CAPTCHAS requiring JavaScript.
- Can’t load or download media elements or webpages which require JavaScript.
- Can’t log into services like webmail which require JavaScript.
Non-JS Related Issues:
- Changing security level requires reconnecting to a bridge as mentioned by @Radar451.
- Changing security level removes current tabs & cookies from the session.
Solutions:
The solutions outlined in this section will be presented in the order they were suggested. If new solutions are suggested after this reply is posted, a moderator is free to append to this section.
Solution #0:
Do nothing. Leave the changes as they are now in 14.5.4 and up, and see what happens.
Pros: No developer changes required, people who like the 14.5.4 changes are happy.
Cons: people who depend on the functionality of the pre-14.5.4 security style will need to adapt using the new changes or resort to the unconventional and not recommended methods described in “Workaround of 14.5.4 changes (Not Recommended)”
Solution #1:
Adding a button under the security level change box to either lock or unlock the ability to change the security settings inside of a single session. This was outlined in the initial post for this thread under “Graphical Depiction”.
Pros: Feature’s potential harms are clearly described, feature is easy to understand, grants user desired freedom or desired security if they so choose.
Cons: Would require 2 separate interfaces which is inefficient for developer upkeep - as mentioned by @donuts and could potentially lead to Browser vulnerabilities or fingerprinting issues in the future. Feature could potentially result in mid-session security level change issues.
Solution #2:
Add a button for ‘Safest’ users to temporarily enable JavaScript for a single webpage or multiple page loads.
Pros: Should be more simple to implement than solution #1 and should not result in fingerprinting or mid-session security change issues.
Cons: Feature is not as expanded or in-depth as solution #3.
Solution #3:
Implement per-site security settings.
Pros: would allow the user to individually control many different aspects of each site they visit, including enable or disable JavaScript as they choose.
Cons: Very hard to implement compared to solution #1 or #2 as mentioned by @thorin in the Gitlab issue: Safest users can no longer downgrade mid-session to temporarily enable JS (#43922) · Issues · The Tor Project / Applications / Tor Browser · GitLab
Workaround of 14.5.4 changes: (Not Recommended)
-Warning-
Venturing into about:config is not recommended and can potentially result in atypical or dangerous browser behavior with regards to anonymity, security, or fingerprinting.
Remember that I am giving you these methods as a random person on the internet who should not be inherently trusted and lacks the in-depth knowledge of a developer with regards to how changing these switches in about:config could negatively affect you. Please be smart and cautious, do not follow a circumvention blindly if you decide to do so.
Working Around SecurityLevel Changes:
This section describes how users who depend on the before 14.5.4 functionality could potentially work around these recent changes to continue to use Tor Browser how they need to.
Method #1 (toggling "javascript.enabled"):
This method retains tabs and cookies, but is the least secure and most finger-printable option you can use.
- start the browser in ‘Safer’ mode.
- venture into about:config
- search for “javascript.enabled” and switch it to false (this should load new sites with JavaScript Disabled).
- test to make sure JavaScript is disabled using something like EFF’s CYT (All JS-Derived Characteristics should read “No JavaScript” except for User agent and HTTP headers)
- If you need JavaScript on a certain tab, switch “javascript.enabled” to true and refresh the target tab (this now makes JavaScript available to either all tabs or just the tab you refresh, I’m not completely sure, assume every tab now can execute JavaScript and prepare accordingly if you desire.)
- Do what you need inside of the JS-enabled tab. (pass CAPTCHA for example)
- Switch “javascript.enabled” back to false and refresh all tabs.
This procedure would be repeated as necessary by the user.
Method #2 ("changing browser.security_level.security_slider"):
Change the “browser.security_level.security_slider” setting, (this flag may still prompt a restart upon changing) as was explained by @Noino and also isn’t generally recommended.
Keeping Tabs when Requiring JS Without Needing about:config:
This option is more secure and less finger-printable than the toggling option, however it only retains tab history and not cookies.
If you would like to stay in ‘Safest’ mode and properly switch to ‘Safer’ mode for a specific tab using the button and would like to keep your tab history (not cookies, they get wiped), the most simple way while keeping things within the browser would be:
- bookmark your tabs in the ‘Safest’ session.
- restart to ‘Safer’ or ‘Standard’.
- load the specific tab you need, do what you need with it.
- switch back to ‘Safest’ mode and load your tabs from bookmarks.
- delete bookmarks.
repeat as necessary.
If you don’t want to use bookmarks, copying tab links into a text editor is an option (although also not recommended, make sure it doesn’t make a temporary swapfile or connect to the internet).
Conclusion & Keeping my Writing Accountable:
I am prone to making minor context mistakes when referencing security modes. For example, I may say ‘Safer’ in a context when I meant ‘Safest’, like I did in my first post as was mentioned by kasia here for your reference (thank you for pointing this out!)
English is my second language and I still have trouble with it sometimes. If you find any context issues concerning my post that are very serious, let me know before I lose access to editing the post and I’ll strike out the mistake and fix it or maybe a moderator can fix it after if I confirm that it’s an issue in a subsequent reply or personal email.
Thanks to everyone for being cooperative and trying to work towards a solution, hopefully we can decide on something that helps everyone out. I will continue to check on the thread semi-frequently.
Finally, if you’re a moderator (donuts specifically) and you believe this post is cluttering up the thread and provides no serious benefit to it regarding consolidation or solution, remove it or don’t let it through. I understand.