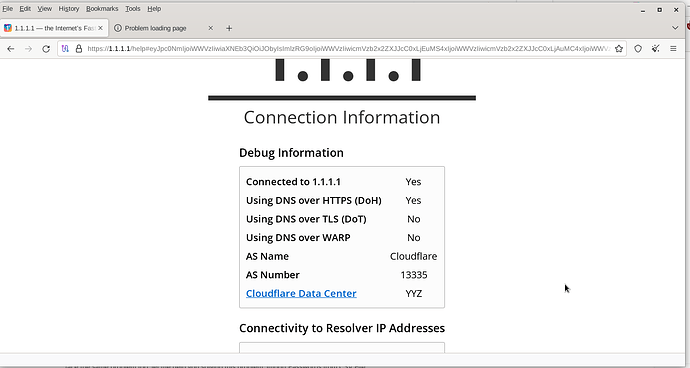
I am using Tor version 13.0.10 on Debian and using firefox 122 and when I go to the Cloudflare site 1.1.1.1/help to view the DNS over HTTPs information, I surprisingly see my location information YYZ and DOH being used. How would this occur ?
What tor browser version are you using? edit: i should read before doing
windows + TB 13.0.10.0
What do you mean by this?
@FranklyFlawless : I suspect the user is using tor with Firefox
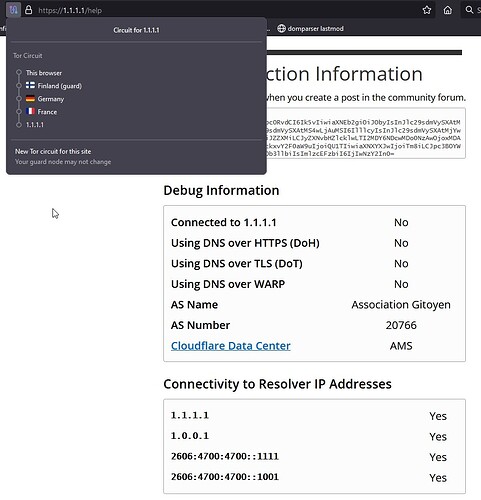
You are coming out of a CA exit node. I get the same when I select CA as exit and get ZRH when I selected a CH exit node and CDG when selecting a FR exit node.
There is nothing suspicious there.
That is what I would expect to see is no or the first three as Tor does not DOH. I am using Debian bookworm. what is your O.S.
Tor should not know my location. tor does not use DNS over HTTPs and when I perform a check of DOH 1.1.1.1/help it gives me the results you see on a Debian linux machine running version 13.0.10
You state “Tor should not know my location. tor does not use DNS over HTTPs”
You are correct. It does not. As I said above, YYZ (Toronto) is simply where that Cloudflare server responding to 1.1.1.1 is actually located. They have them all over the world.
I see nothing in your screenshot which indicates a location other than YYZ. This says to me that you came out of a CA exit node. Tor selects an exit node randomly, and if your country has them, then it is a potential selection. There is NO guarantee that Tor will not use your country for an exit.
Have you tried starting Tor Browser again and checking. Then refresh the page a few times. Do you always get YYZ?
Tried this on Windows 11, Windows 10, and a flavour of Ubuntu Linux 20.04.1 called Zorin. I selected a CA exit and got YYZ. (FYI: ExitNodes {ca} in file torrc)
You mention “Tor version 13.0.10 on Debian and using firefox 122”
Does this mean you proxy Firefox 122 through Tor 13.0.10? Tried this on Win11 and got DOH=yes because my FF 123.0 has this option on.
No idea about that new bridge thing.
You did not answer my question. What does Firefox 122 have to do with your issue?
TO: FranklyFlawless
Yeah I asked the same question.
I tried that experiment and gave my results above. We can see from the initial screenshot that this is not the case. There is that little icon in the top left where you can see the circuit IPs and locations. I see no option in Tor to select DOH but Firefox says it can decide by itself whether it wants to use it or not.
The point is the DOH test provided by cloudflare ran successfully stating I am using DNS over HTTPS as Yes. that should never happen.
Since the upgrade to 13.0.0.12 it has not done it.
Here is something else I noticed which is different. In your initial image I can see the actual IP address we both used (1.1.1.1/help) in the address bar but now, for me, I see one.one.one.one/help
It that Cloudflare or 13.0.12? I never saw DOH thru Tor.
Here is another difference. Look at your initial image then look at the one posted by thorin. Yours says connected to 1.1.1.1 YES and his says NO.
I get YES via my normal connection and NO thru Tor.
Anyway, it is good to know that it is correct now.
1.1.1.1 and one.one.one.one are the same thing.
To check if doh/dot/cf-dns is used, this page tries to connect to {some-uuid}.is-{doh,dot,cf}.help.every1dns.net. These domains resolve only if you use cloudflare’s own resolver. But TorBrowser doesn’t make DNS requests, exit nodes do. So what you are seeing is that this particular exit node appear to use Cloudflare’s DoH endpoint as its resolver. If you try to reload this page with a new circuit, from time to time you’ll see Connected to 1.1.1.1 being alternatively Yes or No (more often No than Yes though). This solely depends on which exit node was picked to connect to cloudflare this time.
Well yes and no. For the purpose of this thread it kinda does the same. There is one (no pun intended) subtle difference.
one.one.one.one is a subdomain of the domain one.one (Denmark) and it has to be resolved. It just happens to resolve to 1.1.1.1
Outside of Tor I can make one.one.one.one resolve to Google’s 8.8.8.8 or IBM’s 9.9.9.9
I know the exit node does the DNS but when you use the IP there is no DNS. Now imagine if the exit node just happens to connect to a rogue DNS resolver (I’m sure there are checks so it cannot) it could send one.one.one.one to wherever it wants. I have no idea why someone would do this.
Cloudflare always sends 1.1.1.1 to as close to you as possible. I just did a tracert and it ended in the city I am in. I then used an external tracert service in Dallas TX and it ended in Dallas. So 1.1.1.1 is wherever Cloudflare says it is. The magic of BGP.
None of this has to do with the conversation in this thread above.
I just wanted to point out that 1.1.1.1 and one.one.one.one are NOT the same thing.
Try one.one.one.one with tracert and with nslookup
Isn’t this discouraged? From the docs.
Don’t use any of the big DNS resolvers (Google, OpenDNS, Quad9, Cloudflare, 4.2.2.1-6) as your primary or fallback DNS resolver to avoid centralization.
You are correct in that link about exit nodes not using big DNS resolvers but as a user I have no control over that. There are no settings in Tor Browser like in vanilla Firefox about DOH or not.
In the three case in this thread (the first two and later my test) we all used 1.1.1.1 and there was no DNS resolving needed.
It’s only after compis reported that it was “fixed” after 13.0.12 that I noticed one.one.one.one in the address bar. It’s not in the two screenshots above.
I have no idea how this occurs.
I have not seen this issue occur again since running 13.0.14 and Tor has removed the option to default to onion sites automatically because of an issue.