I found a very similar topic, but it was specific to snowflake, while I’m considering webtunnel (and perhaps obfs4), which don’t make separate STUN connection AFAIK.
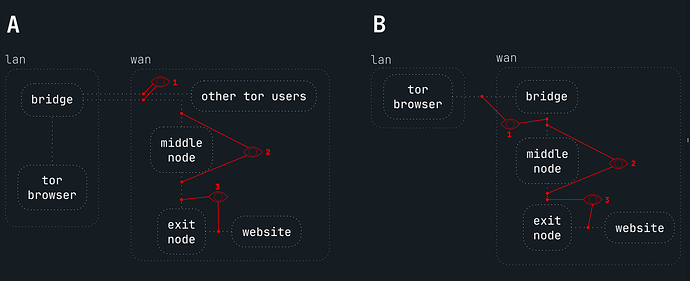
Could you please help me understand if using a self-hosted (at home) tor bridge as as your own entry node considered harmful for your anonymity?
Is it a problem that the first hop is at your own IP address and the other two hops are external? If so, why or why not? Does it violate any fundamental assumptions behind tor circuits? Are you aware of any academic studies or other publications/documentation that discusses it in more detail?
Advantages of setting up a tor bridge with sole purpose of blending your traffic with other users . Especially as I read (in this guide) that tor can let you reuse the already established tcp connection. directly via the same connection. Other users use your bridge on a regular basis together with you and perhaps also your hidden services. ISP monitoring of your exact connection times should be harder (not sure how much exactly, but still)? I don’t understand why hosting a bridge outside of your geographic location is necessary?
Please see network topology diagram below showing the two scenarios. 1 with bridge hosted on your own network and one with an external bridge. Is any one weaker than the other in terms of de-anonymization risks (as described above)?
also I found in the original 2004 white paper on tor:
“If Alice only ever uses two hops, then both ORs can be certain that by colluding they will learn about Alice and Bob. In our current approach, Alice always chooses at least three nodes unrelated to herself and her destination.” But could someone explain why they need to be unrelated?
Does it have to do only with correlation attack? Has it ever been more precisely quantified?
I’ve also heard that entry and exit nodes are the most important ones. Wouldn’t increased security of a self-hosted bridge outweigh any potential drawbacks?