Sorry for not seeing this until now.
Unfortunately I don’t have time to read the paper, however years ago, I read the Snowflake page and the technical overview.
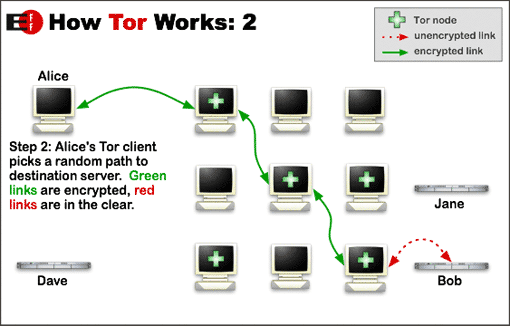
Currently my biggest questions revolve around how it integrates with all the other diagrams we’ve seen of the traditional 3-hop route. (Putting aside onion services to keep it simple.)
In this paper, there’s a new (to me) diagram but it’s still not conveying to me how it fits in to tor’s 3-hop strategy.
I’m sure you have much deeper knowledge of tor than I do, so please excuse me if I goof up my words.
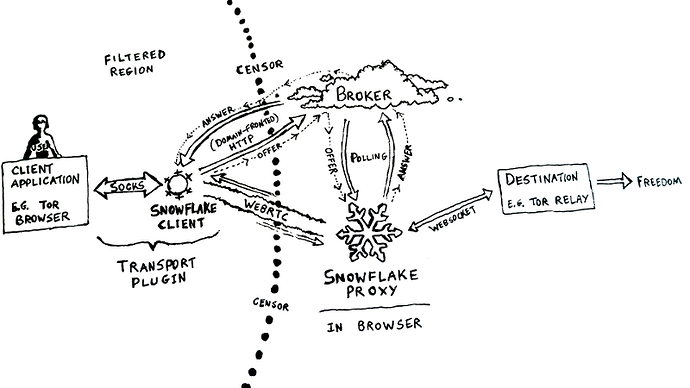
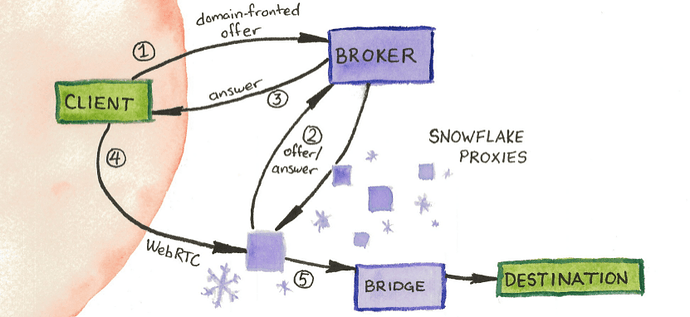
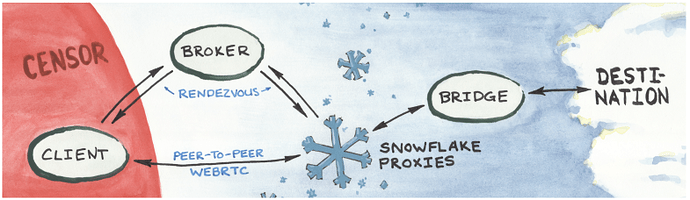
This is the only thing I see as it relates: snowflake proxy, bridge, destination.
The snowflake proxy is, let’s say me, running (in my case) a stand alone snowflake proxy. This made me think I was akin to a guard, or a bridge; i.e. the first computer on their path to a middle node, etc.
But confusingly the next hop (in all the snowflake diagrams I’ve seen) is called a “bridge,” which has a specific meaning in tor land. My understanding is that tor-bridges are (mainly*) unpublished guard nodes, i.e. the first hop of the 3-hop route. Is this snowflake-bridge an actual tor-bridge (hop 1) or is it, as it looks in the diagrams, hop 2? And is it a published tor relay, or an actual unpublished bridge?
Then there’s the “destination” as the third item in the diagram. Is this “destination” the exit node (hop 3) or is it truly the destination the exit node contacts on behalf of the tor user?
Can the traditional 3-hop tor diagram be laid on top of the Snowflake architecture diagram for those of us who like to think visually? I think this would be a boon. There are scads of 3-hop diagrams online, lots of people are excited to explain tor. But where does SP end and tor begin?
My only other comment is perhaps nitpicking, and it didn’t strike me as much when I read the technical overview, but I admit I read a little past the diagram on this most recent paper and wished for a synonym for “rendezvous” to be used, given its specific meaning to onion site connections. Rendezvous without a word prefacing it, i.e. onion rendezvous, snowflake rendezvous, could lead to confusion in excerpts/conversation/presentations/non-technical writings, and make it more difficult to locate specifics during text searches.
I wish you luck and hope to see the video of the presentation!
* It’s been even longer since I studied Tor’s man page, but I think I recall one can enter a bridge key to be used as an exit.