@Vort How can i test #1 ? I will research how clean the keys #2.
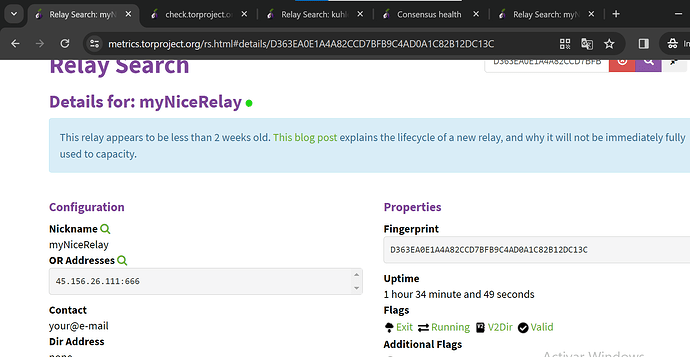
@Felix 45.156.26.111 is the public ip address of VDS, the 77.77.77.2 is a local ip address from a specific interface(tun0) for connect to my VDS with VPN and route all traffic to my home device(CG-NAT bypass).
I wanna add some new logs, im still running it just for see if something change:
Apr 01 04:53:07 debian-ab433f423 Tor[745656]: Heartbeat: Tor's uptime is 3 days 0:00 hours, with 0 circuits open. I've sent 55.75 MB and received 50.53 MB. I've received 18 connections on IPv4 and 0 on IPv6. I've made 2361 connections with IPv4 and 0 with IPv6.
Apr 01 04:53:07 debian-ab433f423 Tor[745656]: While bootstrapping, fetched this many bytes: 578851 (consensus network-status fetch); 53814 (microdescriptor fetch)
Apr 01 04:53:07 debian-ab433f423 Tor[745656]: Circuit handshake stats since last time: 0/0 TAP, 0/0 NTor.
Apr 01 04:53:07 debian-ab433f423 Tor[745656]: Since startup we initiated 0 and received 0 v1 connections; initiated 0 and received 0 v2 connections; initiated 0 and received 0 v3 connections; initiated 0 and received 0 v4 connections; initiated 14 and received 2 v5 connections.
Apr 01 04:53:07 debian-ab433f423 Tor[745656]: Heartbeat: DoS mitigation since startup: 0 circuits killed with too many cells, 0 circuits rejected, 0 marked addresses, 0 marked addresses for max queue, 0 same address concurrent connections rejected, 0 connections rejected, 0 single hop clients refused, 0 INTRODUCE2 rejected.
Apr 01 07:57:04 debian-ab433f423 Tor[745656]: New control connection opened.
Apr 01 08:42:17 debian-ab433f423 Tor[745656]: New control connection opened.
Apr 01 08:54:42 debian-ab433f423 Tor[745656]: New control connection opened.
Apr 01 09:11:20 debian-ab433f423 Tor[745656]: New control connection opened.
Apr 01 10:53:07 debian-ab433f423 Tor[745656]: Heartbeat: It seems like we are not in the cached consensus.
Apr 01 10:53:07 debian-ab433f423 Tor[745656]: Heartbeat: Tor's uptime is 3 days 6:00 hours, with 0 circuits open. I've sent 55.75 MB and received 50.53 MB. I've received 21 connections on IPv4 and 0 on IPv6. I've made 2370 connections with IPv4 and 0 with IPv6.
Apr 01 10:53:07 debian-ab433f423 Tor[745656]: While bootstrapping, fetched this many bytes: 578851 (consensus network-status fetch); 53814 (microdescriptor fetch)
Apr 01 10:53:07 debian-ab433f423 Tor[745656]: Circuit handshake stats since last time: 0/0 TAP, 0/0 NTor.
Apr 01 10:53:07 debian-ab433f423 Tor[745656]: Since startup we initiated 0 and received 0 v1 connections; initiated 0 and received 0 v2 connections; initiated 0 and received 0 v3 connections; initiated 0 and received 0 v4 connections; initiated 14 and received 2 v5 connections.
Apr 01 10:53:07 debian-ab433f423 Tor[745656]: Heartbeat: DoS mitigation since startup: 0 circuits killed with too many cells, 0 circuits rejected, 0 marked addresses, 0 marked addresses for max queue, 0 same address concurrent connections rejected, 0 connections rejected, 0 single hop clients refused, 0 INTRODUCE2 rejected.
Apr 01 16:53:07 debian-ab433f423 Tor[745656]: Heartbeat: It seems like we are not in the cached consensus.
Apr 01 16:53:07 debian-ab433f423 Tor[745656]: Heartbeat: Tor's uptime is 3 days 12:00 hours, with 0 circuits open. I've sent 55.75 MB and received 50.53 MB. I've received 32 connections on IPv4 and 0 on IPv6. I've made 2371 connections with IPv4 and 0 with IPv6.
Apr 01 16:53:07 debian-ab433f423 Tor[745656]: While bootstrapping, fetched this many bytes: 578851 (consensus network-status fetch); 53814 (microdescriptor fetch)
Apr 01 16:53:07 debian-ab433f423 Tor[745656]: Circuit handshake stats since last time: 0/0 TAP, 0/0 NTor.
Apr 01 16:53:07 debian-ab433f423 Tor[745656]: Since startup we initiated 0 and received 0 v1 connections; initiated 0 and received 0 v2 connections; initiated 0 and received 0 v3 connections; initiated 0 and received 0 v4 connections; initiated 14 and received 2 v5 connections.
Apr 01 16:53:07 debian-ab433f423 Tor[745656]: Heartbeat: DoS mitigation since startup: 0 circuits killed with too many cells, 0 circuits rejected, 0 marked addresses, 0 marked addresses for max queue, 0 same address concurrent connections rejected, 0 connections rejected, 0 single hop clients refused, 0 INTRODUCE2 rejected.
Apr 01 22:53:07 debian-ab433f423 Tor[745656]: Heartbeat: It seems like we are not in the cached consensus.
Apr 01 22:53:07 debian-ab433f423 Tor[745656]: Heartbeat: Tor's uptime is 3 days 18:00 hours, with 0 circuits open. I've sent 55.75 MB and received 50.53 MB. I've received 34 connections on IPv4 and 0 on IPv6. I've made 2372 connections with IPv4 and 0 with IPv6.
Apr 01 22:53:07 debian-ab433f423 Tor[745656]: While bootstrapping, fetched this many bytes: 578851 (consensus network-status fetch); 53814 (microdescriptor fetch)
Apr 01 22:53:07 debian-ab433f423 Tor[745656]: Circuit handshake stats since last time: 0/0 TAP, 0/0 NTor.
Apr 01 22:53:07 debian-ab433f423 Tor[745656]: Since startup we initiated 0 and received 0 v1 connections; initiated 0 and received 0 v2 connections; initiated 0 and received 0 v3 connections; initiated 0 and received 0 v4 connections; initiated 14 and received 2 v5 connections.
Apr 01 22:53:07 debian-ab433f423 Tor[745656]: Heartbeat: DoS mitigation since startup: 0 circuits killed with too many cells, 0 circuits rejected, 0 marked addresses, 0 marked addresses for max queue, 0 same address concurrent connections rejected, 0 connections rejected, 0 single hop clients refused, 0 INTRODUCE2 rejected.
Apr 02 04:53:07 debian-ab433f423 Tor[745656]: Heartbeat: It seems like we are not in the cached consensus.
Apr 02 04:53:07 debian-ab433f423 Tor[745656]: Heartbeat: Tor's uptime is 4 days 0:00 hours, with 0 circuits open. I've sent 55.75 MB and received 50.53 MB. I've received 156 connections on IPv4 and 0 on IPv6. I've made 2380 connections with IPv4 and 0 with IPv6.
Apr 02 04:53:07 debian-ab433f423 Tor[745656]: While bootstrapping, fetched this many bytes: 578851 (consensus network-status fetch); 53814 (microdescriptor fetch)
Apr 02 04:53:07 debian-ab433f423 Tor[745656]: Circuit handshake stats since last time: 0/0 TAP, 0/0 NTor.
Apr 02 04:53:07 debian-ab433f423 Tor[745656]: Since startup we initiated 0 and received 0 v1 connections; initiated 0 and received 0 v2 connections; initiated 0 and received 0 v3 connections; initiated 0 and received 0 v4 connections; initiated 14 and received 2 v5 connections.
Apr 02 04:53:07 debian-ab433f423 Tor[745656]: Heartbeat: DoS mitigation since startup: 0 circuits killed with too many cells, 0 circuits rejected, 0 marked addresses, 0 marked addresses for max queue, 0 same address concurrent connections rejected, 0 connections rejected, 0 single hop clients refused, 0 INTRODUCE2 rejected.
Apr 02 09:43:38 debian-ab433f423 Tor[745656]: New control connection opened.
I gonna clean the keys and keep running it for next 3 days and see if something change.