Thank you!
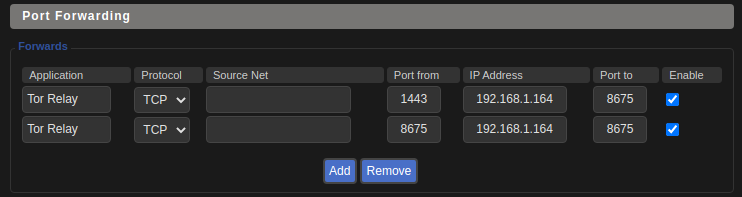
Here are my port forwarding settings before pointing from 1443 to 1443:
Here is my /etc/tor/torrc output before pointing from 1443 to 1443:
Sep 16 01:55:10 macrohumanity systemd[1]: Starting Anonymizing overlay network for TCP...
Sep 16 01:55:10 macrohumanity tor[961]: Sep 16 01:55:10.490 [notice] Tor 0.4.7.10 running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.2, Zlib 1.2.11, L>
Sep 16 01:55:10 macrohumanity tor[961]: Sep 16 01:55:10.490 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://support.torproje>
Sep 16 01:55:10 macrohumanity tor[961]: Sep 16 01:55:10.494 [notice] Read configuration file "/usr/share/tor/tor-service-defaults-torrc".
Sep 16 01:55:10 macrohumanity tor[961]: Sep 16 01:55:10.494 [notice] Read configuration file "/etc/tor/torrc".
Sep 16 01:55:10 macrohumanity tor[961]: Sep 16 01:55:10.498 [notice] Based on detected system memory, MaxMemInQueues is set to 5769 MB. You can override this>
Sep 16 01:55:10 macrohumanity tor[961]: Configuration was valid
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.619 [notice] Tor 0.4.7.10 running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.2, Zlib 1.2.11, L>
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.619 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://support.torproje>
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.619 [notice] Read configuration file "/usr/share/tor/tor-service-defaults-torrc".
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.619 [notice] Read configuration file "/etc/tor/torrc".
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.621 [notice] Based on detected system memory, MaxMemInQueues is set to 5769 MB. You can override this>
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.667 [notice] Opening Socks listener on 127.0.0.1:9050
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.667 [notice] Opened Socks listener connection (ready) on 127.0.0.1:9050
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.667 [notice] Opening OR listener on 0.0.0.0:8675
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.667 [notice] Opened OR listener connection (ready) on 0.0.0.0:8675
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.667 [notice] Opening Extended OR listener on 127.0.0.1:0
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.667 [notice] Extended OR listener listening on port 46857.
Sep 16 01:55:10 macrohumanity tor[964]: Sep 16 01:55:10.667 [notice] Opened Extended OR listener connection (ready) on 127.0.0.1:46857
Sep 16 01:55:10 macrohumanity Tor[964]: We compiled with OpenSSL 30000020: OpenSSL 3.0.2 15 Mar 2022 and we are running with OpenSSL 30000020: 3.0.2. These t>
Sep 16 01:55:10 macrohumanity Tor[964]: Tor 0.4.7.10 running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.2, Zlib 1.2.11, Liblzma 5.2.5, Libzstd 1.4.8 a>
Sep 16 01:55:10 macrohumanity Tor[964]: Tor can't help you if you use it wrong! Learn how to be safe at https://support.torproject.org/faq/staying-anonymous/
Sep 16 01:55:10 macrohumanity Tor[964]: Read configuration file "/usr/share/tor/tor-service-defaults-torrc".
Sep 16 01:55:10 macrohumanity Tor[964]: Read configuration file "/etc/tor/torrc".
Sep 16 01:55:10 macrohumanity Tor[964]: Based on detected system memory, MaxMemInQueues is set to 5769 MB. You can override this by setting MaxMemInQueues by>
Sep 16 01:55:10 macrohumanity Tor[964]: Opening Socks listener on 127.0.0.1:9050
Sep 16 01:55:10 macrohumanity Tor[964]: Opened Socks listener connection (ready) on 127.0.0.1:9050
Sep 16 01:55:10 macrohumanity Tor[964]: Opening OR listener on 0.0.0.0:8675
Sep 16 01:55:10 macrohumanity Tor[964]: Opened OR listener connection (ready) on 0.0.0.0:8675
Sep 16 01:55:10 macrohumanity Tor[964]: Opening Extended OR listener on 127.0.0.1:0
Sep 16 01:55:10 macrohumanity Tor[964]: Extended OR listener listening on port 46857.
Sep 16 01:55:10 macrohumanity Tor[964]: Opened Extended OR listener connection (ready) on 127.0.0.1:46857
Sep 16 01:55:12 macrohumanity Tor[964]: Parsing GEOIP IPv4 file /usr/share/tor/geoip.
Sep 16 01:55:12 macrohumanity Tor[964]: Parsing GEOIP IPv6 file /usr/share/tor/geoip6.
Sep 16 01:55:12 macrohumanity Tor[964]: Configured to measure statistics. Look for the *-stats files that will first be written to the data directory in 24 h>
Sep 16 01:55:13 macrohumanity Tor[964]: Your Tor server's identity key fingerprint is <private>
Sep 16 01:55:13 macrohumanity Tor[964]: Your Tor bridge's hashed identity key fingerprint is <private>
Sep 16 01:55:13 macrohumanity Tor[964]: Your Tor server's identity key <private> fingerprint is 'macrohumanity <private>
Sep 16 01:55:13 macrohumanity Tor[964]: You can check the status of your bridge relay at https://bridges.torproject.org/status?id=<private>
Sep 16 01:55:13 macrohumanity Tor[964]: Bootstrapped 0% (starting): Starting
Sep 16 01:55:14 macrohumanity Tor[964]: Starting with guard context "default"
Sep 16 01:55:26 macrohumanity Tor[964]: Signaled readiness to systemd
Sep 16 01:55:26 macrohumanity systemd[1]: Started Anonymizing overlay network for TCP.
Sep 16 01:55:26 macrohumanity Tor[964]: Registered server transport 'obfs4' at '[::]:1443'
Sep 16 01:55:27 macrohumanity Tor[964]: External address seen and suggested by a directory authority: 174.63.120.155
Sep 16 01:55:27 macrohumanity Tor[964]: Bootstrapped 5% (conn): Connecting to a relay
Sep 16 01:55:27 macrohumanity Tor[964]: Opening Socks listener on /run/tor/socks
Sep 16 01:55:27 macrohumanity Tor[964]: Opened Socks listener connection (ready) on /run/tor/socks
Sep 16 01:55:27 macrohumanity Tor[964]: Opening Control listener on /run/tor/control
Sep 16 01:55:27 macrohumanity Tor[964]: Opened Control listener connection (ready) on /run/tor/control
Sep 16 01:55:27 macrohumanity Tor[964]: Bootstrapped 10% (conn_done): Connected to a relay
Sep 16 01:55:28 macrohumanity Tor[964]: Bootstrapped 14% (handshake): Handshaking with a relay
Sep 16 01:55:28 macrohumanity Tor[964]: Bootstrapped 15% (handshake_done): Handshake with a relay done
Sep 16 01:55:28 macrohumanity Tor[964]: Bootstrapped 75% (enough_dirinfo): Loaded enough directory info to build circuits
Sep 16 01:55:28 macrohumanity Tor[964]: Bootstrapped 90% (ap_handshake_done): Handshake finished with a relay to build circuits
Sep 16 01:55:28 macrohumanity Tor[964]: Bootstrapped 95% (circuit_create): Establishing a Tor circuit
Sep 16 01:55:30 macrohumanity Tor[964]: Bootstrapped 100% (done): Done
Sep 16 01:55:30 macrohumanity Tor[964]: Now checking whether IPv4 ORPort 174.63.120.155:8675 is reachable... (this may take up to 20 minutes -- look for log >
Sep 16 01:55:32 macrohumanity Tor[964]: Self-testing indicates your ORPort 174.63.120.155:8675 is reachable from the outside. Excellent. Publishing server de>
Sep 16 01:55:41 macrohumanity Tor[964]: Performing bandwidth self-test...done.
Sep 16 07:55:27 macrohumanity Tor[964]: Heartbeat: Tor's uptime is 6:00 hours, with 0 circuits open. I've sent 2.38 MB and received 7.19 MB. I've received 23>
Sep 16 07:55:27 macrohumanity Tor[964]: While not bootstrapping, fetched this many bytes: 4669117 (server descriptor fetch); 355 (server descriptor upload); >
Sep 16 07:55:27 macrohumanity Tor[964]: Heartbeat: Since last heartbeat message, I have seen 0 unique clients.
Sep 17 18:46:34 macrohumanity Tor[964]: Your system clock just jumped 106173 seconds forward; assuming established circuits no longer work.
Sep 17 18:46:34 macrohumanity Tor[964]: Our directory information is no longer up-to-date enough to build circuits: We have no recent usable consensus.
Sep 17 18:46:42 macrohumanity Tor[964]: We now have enough directory information to build circuits.
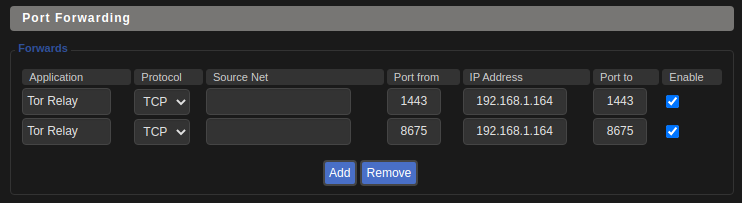
Here are my port forwarding settings after pointing from 1443 to 1443:
Here is my /etc/tor/torrc output after pointing from 1443 to 1443:
Sep 17 21:48:42 macrohumanity systemd[1]: Starting Anonymizing overlay network for TCP...
Sep 17 21:48:42 macrohumanity tor[964]: Sep 17 21:48:42.878 [notice] Tor 0.4.7.10 running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.2, Zlib 1.2.11, Liblzma 5.2.5, Libzstd 1.4.8 and Glibc 2.35 as libc.
Sep 17 21:48:42 macrohumanity tor[964]: Sep 17 21:48:42.879 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://support.torproject.org/faq/staying-anonymous/
Sep 17 21:48:42 macrohumanity tor[964]: Sep 17 21:48:42.880 [notice] Read configuration file "/usr/share/tor/tor-service-defaults-torrc".
Sep 17 21:48:42 macrohumanity tor[964]: Sep 17 21:48:42.882 [notice] Read configuration file "/etc/tor/torrc".
Sep 17 21:48:42 macrohumanity tor[964]: Sep 17 21:48:42.891 [notice] Based on detected system memory, MaxMemInQueues is set to 5769 MB. You can override this by setting MaxMemInQueues by hand.
Sep 17 21:48:42 macrohumanity tor[964]: Configuration was valid
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.005 [notice] Tor 0.4.7.10 running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.2, Zlib 1.2.11, Liblzma 5.2.5, Libzstd 1.4.8 and Glibc 2.35 as libc.
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.008 [notice] Tor can't help you if you use it wrong! Learn how to be safe at https://support.torproject.org/faq/staying-anonymous/
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.008 [notice] Read configuration file "/usr/share/tor/tor-service-defaults-torrc".
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.008 [notice] Read configuration file "/etc/tor/torrc".
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.010 [notice] Based on detected system memory, MaxMemInQueues is set to 5769 MB. You can override this by setting MaxMemInQueues by hand.
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.020 [notice] Opening Socks listener on 127.0.0.1:9050
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.020 [notice] Opened Socks listener connection (ready) on 127.0.0.1:9050
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.020 [notice] Opening OR listener on 0.0.0.0:8675
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.021 [notice] Opened OR listener connection (ready) on 0.0.0.0:8675
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.021 [notice] Opening Extended OR listener on 127.0.0.1:0
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.021 [notice] Extended OR listener listening on port 39189.
Sep 17 21:48:43 macrohumanity tor[969]: Sep 17 21:48:43.022 [notice] Opened Extended OR listener connection (ready) on 127.0.0.1:39189
Sep 17 21:48:43 macrohumanity Tor[969]: We compiled with OpenSSL 30000020: OpenSSL 3.0.2 15 Mar 2022 and we are running with OpenSSL 30000020: 3.0.2. These two versions should be binary compatible.
Sep 17 21:48:43 macrohumanity Tor[969]: Tor 0.4.7.10 running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.2, Zlib 1.2.11, Liblzma 5.2.5, Libzstd 1.4.8 and Glibc 2.35 as libc.
Sep 17 21:48:43 macrohumanity Tor[969]: Tor can't help you if you use it wrong! Learn how to be safe at https://support.torproject.org/faq/staying-anonymous/
Sep 17 21:48:43 macrohumanity Tor[969]: Read configuration file "/usr/share/tor/tor-service-defaults-torrc".
Sep 17 21:48:43 macrohumanity Tor[969]: Read configuration file "/etc/tor/torrc".
Sep 17 21:48:43 macrohumanity Tor[969]: Based on detected system memory, MaxMemInQueues is set to 5769 MB. You can override this by setting MaxMemInQueues by hand.
Sep 17 21:48:43 macrohumanity Tor[969]: Opening Socks listener on 127.0.0.1:9050
Sep 17 21:48:43 macrohumanity Tor[969]: Opened Socks listener connection (ready) on 127.0.0.1:9050
Sep 17 21:48:43 macrohumanity Tor[969]: Opening OR listener on 0.0.0.0:8675
Sep 17 21:48:43 macrohumanity Tor[969]: Opened OR listener connection (ready) on 0.0.0.0:8675
Sep 17 21:48:43 macrohumanity Tor[969]: Opening Extended OR listener on 127.0.0.1:0
Sep 17 21:48:43 macrohumanity Tor[969]: Extended OR listener listening on port 39189.
Sep 17 21:48:43 macrohumanity Tor[969]: Opened Extended OR listener connection (ready) on 127.0.0.1:39189
Sep 17 21:48:45 macrohumanity Tor[969]: Parsing GEOIP IPv4 file /usr/share/tor/geoip.
Sep 17 21:48:45 macrohumanity Tor[969]: Parsing GEOIP IPv6 file /usr/share/tor/geoip6.
Sep 17 21:48:45 macrohumanity Tor[969]: Configured to measure statistics. Look for the *-stats files that will first be written to the data directory in 24 hours from now.
Sep 17 21:48:45 macrohumanity Tor[969]: Your Tor server's identity key fingerprint is 'macrohumanity 6CF1FA5CB4FEA1C9A739BCBC55619402FD1564BD'
Sep 17 21:48:45 macrohumanity Tor[969]: Your Tor bridge's hashed identity key fingerprint is 'macrohumanity 2D803B83F0038B24C77A16FC5196790AB1BD6093'
Sep 17 21:48:45 macrohumanity Tor[969]: Your Tor server's identity key ed25519 fingerprint is 'macrohumanity VzOOpB2OlPwO1+vuYxzA5Y1AKZyTG1ZCtbnvRR2JXVM'
Sep 17 21:48:45 macrohumanity Tor[969]: You can check the status of your bridge relay at https://bridges.torproject.org/status?id=2D803B83F0038B24C77A16FC5196790AB1BD6093
Sep 17 21:48:45 macrohumanity Tor[969]: Bootstrapped 0% (starting): Starting
Sep 17 21:48:46 macrohumanity Tor[969]: Starting with guard context "default"
Sep 17 21:49:00 macrohumanity Tor[969]: Signaled readiness to systemd
Sep 17 21:49:00 macrohumanity systemd[1]: Started Anonymizing overlay network for TCP.
Sep 17 21:49:00 macrohumanity Tor[969]: Registered server transport 'obfs4' at '[::]:1443'
Sep 17 21:49:02 macrohumanity Tor[969]: Bootstrapped 5% (conn): Connecting to a relay
Sep 17 21:49:02 macrohumanity Tor[969]: Opening Socks listener on /run/tor/socks
Sep 17 21:49:02 macrohumanity Tor[969]: Opened Socks listener connection (ready) on /run/tor/socks
Sep 17 21:49:02 macrohumanity Tor[969]: Opening Control listener on /run/tor/control
Sep 17 21:49:02 macrohumanity Tor[969]: Opened Control listener connection (ready) on /run/tor/control
Sep 17 21:49:02 macrohumanity Tor[969]: Bootstrapped 10% (conn_done): Connected to a relay
Sep 17 21:49:02 macrohumanity Tor[969]: Bootstrapped 14% (handshake): Handshaking with a relay
Sep 17 21:49:02 macrohumanity Tor[969]: Bootstrapped 15% (handshake_done): Handshake with a relay done
Sep 17 21:49:02 macrohumanity Tor[969]: Bootstrapped 75% (enough_dirinfo): Loaded enough directory info to build circuits
Sep 17 21:49:02 macrohumanity Tor[969]: Bootstrapped 90% (ap_handshake_done): Handshake finished with a relay to build circuits
Sep 17 21:49:02 macrohumanity Tor[969]: Bootstrapped 95% (circuit_create): Establishing a Tor circuit
Sep 17 21:49:04 macrohumanity Tor[969]: Bootstrapped 100% (done): Done
Sep 17 21:49:04 macrohumanity Tor[969]: Now checking whether IPv4 ORPort 174.63.120.155:8675 is reachable... (this may take up to 20 minutes -- look for log messages indicating success)
Sep 17 21:49:05 macrohumanity Tor[969]: Self-testing indicates your ORPort 174.63.120.155:8675 is reachable from the outside. Excellent. Publishing server descriptor.
Sep 17 21:51:06 macrohumanity Tor[969]: Performing bandwidth self-test...done.
Sep 18 03:49:01 macrohumanity Tor[969]: Heartbeat: Tor's uptime is 6:00 hours, with 22 circuits open. I've sent 301.93 MB and received 299.02 MB. I've received 70 connections on IPv4 and 0 on IPv6. I've made 222 connections with IPv4 and 0 with IPv6.
Sep 18 03:49:01 macrohumanity Tor[969]: While not bootstrapping, fetched this many bytes: 4142846 (server descriptor fetch); 363 (server descriptor upload); 372199 (consensus network-status fetch); 26963 (microdescriptor fetch)
Sep 18 03:49:01 macrohumanity Tor[969]: Heartbeat: Since last heartbeat message, I have seen 5 unique clients.
Sep 18 05:01:04 macrohumanity Tor[969]: No circuits are opened. Relaxed timeout for circuit 224 (a General-purpose client 1-hop circuit in state doing handshakes with channel state open) to 60000ms. However, it appears the circuit has timed out anyway.
Sep 18 05:22:33 macrohumanity Tor[969]: Your network connection speed appears to have changed. Resetting timeout to 60000ms after 18 timeouts and 656 buildtimes.
Sep 18 09:49:01 macrohumanity Tor[969]: Heartbeat: Tor's uptime is 12:00 hours, with 16 circuits open. I've sent 353.13 MB and received 358.56 MB. I've received 136 connections on IPv4 and 0 on IPv6. I've made 351 connections with IPv4 and 0 with IPv6.
Sep 18 09:49:01 macrohumanity Tor[969]: While not bootstrapping, fetched this many bytes: 9119901 (server descriptor fetch); 741 (server descriptor upload); 808990 (consensus network-status fetch); 96025 (microdescriptor fetch)
Sep 18 09:49:01 macrohumanity Tor[969]: Heartbeat: Since last heartbeat message, I have seen 5 unique clients.
5 unique clients! Very awesome.
Aside from this change, an active DD-WRT OpenVPN client seemed to be a culprit during testing. My next project will be to find a way to run my bridge along side of an DD-WRT OpenVPN client.
Thank a lot, everyone